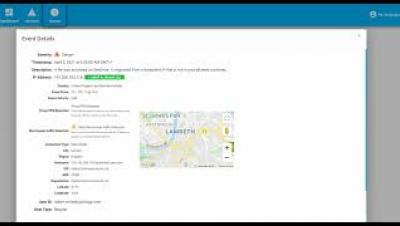
Asymmetrical threats in Cybersecurity
Security and defense theory are inextricably entwined. Consider medieval castles. They were designed as a defensive mechanism that provided security to those within, most of whom were simply civilians hiding behind the walls for protection from invaders. Within cybersecurity, multiple concepts from defense and war theory can be applied to better address the cyber risks facing organizations. In fact, the term Bastion Host refers to a Bastion which has very militaristic connotations.