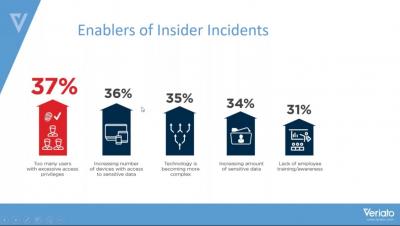
5 employee cyber security training questions you need to ask
Chances are your organization already addresses cyber security to some extent in new employee onboarding. Whether that’s traditional training videos on cyber security that employees watch on their own time, presentations by IT, or brochures, most employees know that their companies have cyber security protocol and best practices. But how many of your employees actually know what the protocol and practices are?