How Does Insider Threat Detection Work & Why is it Crucial?
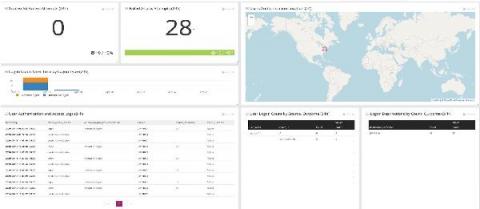
Attaining a strong cyber security posture is a multi-layered process and includes various essential components. Among those, insider threat detection holds unignorable importance. Therefore, it is crucial to obtain a deeper understanding of what insider threat detection is. Basically, an insider threat is a security risk that’s originated within the boundaries of the organization itself. Unlike outside attacks, insider threats are mainly caused by employees.