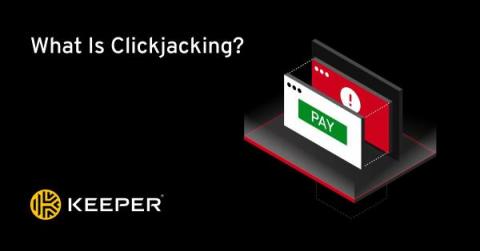
What Is Clickjacking?
Clickjacking, also known as a clickjacking attack or a clickjack, is a cyberattack in which hidden links trick users into completing an unintended action which results in the exposure of sensitive information and hacking. Keep reading to understand more about clickjacking and how it works.