Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2022
How to prevent a rootkit attack before it is too late?
A rootkit is a malicious software program that helps cybercriminals infiltrate a system and take control. Hackers use rootkits to carry out espionage, data theft, deploy other malware such as ransomware, and all without leaving a trace. Once a rootkit is installed on a device, it can intercept system calls, replace software and processes and be part of a larger exploit kit containing other modules such as keyloggers, data theft malware, or even cryptocurrency mining malware.
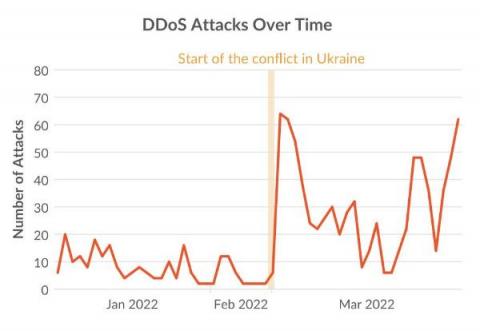
How the Russia-Ukraine conflict changed cyber attacks: More attacks, More DDoS
The conflict between Russia and Ukraine includes a cyberwarfare component with government-supported threat actors and civilian hacktivists taking sides. The goals of disrupting IT infrastructure and utilities have led to a 4-fold increase in DDoS attacks between 4Q21 and 1Q22. Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub.
9 Steps to Mitigate Ransomware Attacks for Your Business
Ransomware attacks have become so prevalent in recent years that it’s no longer a matter of “if” your business may be the victim of a ransomware attack, but “when.” In fact, in 2021, 37% of global organizations reported that they were the victim of a ransomware attack. To mitigate the impact and probability of ransomware on your business, you must continuously look for new ways to secure your network and maintain continuous cybersecurity monitoring.
How Arctic Wolf Disrupts Business Email Compromise Attacks
5 Tips for protecting your connected vehicle against Cyberattacks
As more connected vehicles hit the road, cyberattacks are increasing. Deloitte estimates that there will be over 470 million connected cars in use by 2025 if their popularity continues to grow at the current rate. And because each connected car produces about 25 GB of data every hour, they are a tempting challenge for cybercriminals and bad actors with malicious intent.
How Cyberwar is Wreaking Havoc on Small Businesses
As the world continues to change, so does the nature of warfare, where the Internet has become the main battleground for most of the world’s conflicts. But where is this headed? Cyberattacks have been around for much longer than you may think. The first worm was created by Bob Thomas in 1971: a malicious software that replicates itself, using some of the first world computers to spread to others.
Extortion in Cloud Storage
Extortion can simply be defined as “the practice of obtaining benefit through coercion.“ Data and cloud extortion schemes occur when precious data and/or access is stolen by an attacker that promises to restore it through payment or other demands. In this article, we’ll cover some common or uncommon extortion schemes, and highlight ways to detect and avoid falling prey to demands.
Bypassing MFA with the Pass-the-Cookie Attack
Multi-factor authentication (MFA) is a great way to increase both on-premises and cloud security. With MFA in place, when a user logs on, they are required to provide not only their user ID and password but another authentication factor, such as a code sent to their phone. This process reduces the attack surface by preventing adversaries with stolen user credentials from logging on. However, MFA is not a cybersecurity panacea.
Cyberattacks are targeting smaller healthcare companies and specialty clinics. But why?
The healthcare industry has been a favored target for cybercriminals for many years. In the first half of 2022 alone, 324 attacks against healthcare organizations have been reported. Attackers have primarily focused on large hospitals in years past, but there has been a sudden switch to smaller healthcare companies and specialty clinics. There seems to be a clear trend in attacks against the healthcare industry, and that trend includes targeting smaller healthcare companies and clinics.
Great Power(Shell) doesn't always come with great responsibility: Sometimes, SIEM is all you need
Fileless threats are on the rise. These threats occur when cybercriminals use pre-existing software in victims’ systems to carry out attacks, instead of using a malicious attachment or file. More often than not, a criminal’s favorite tool for a fileless attack is PowerShell.
MFA Prompt bombing: What you need to know
Have you ever had to set up your Gmail account on a secondary device, such as your tablet, and when you tried to login, verification prompts were sent to your original device to confirm that the login attempt was done by you? You confirmed the login, and that ended it. That is exactly what happened to an Uber employee whose account was compromised.
Omdia On the Radar: Cyberpion offers a platform to reduce external attack surfaces
Importance And Benefits Of Cloud-Based Security Systems
Cyber Threats on Sale - A Black Friday Special Intelligence Report
General Overview: Cyber Threats in Todays Society
Cyber threats are a big deal in today’s society. It seems like every other day, there is a new scam or cyber attack that is making the rounds. In this blog post, we will take a look at some of the biggest threats and scams that you need to be aware of. We will also discuss how to protect yourself from these attacks.
Killnet Claims Attacks Against Starlink, Whitehouse.gov, and United Kingdom Websites
Pro-Russian threat actor group Killnet claims to have launched DDoS attacks against Starlink and the United States’ government website whitehouse.gov. Starlink is a satellite internet service company operated by SpaceX. In 2019, SpaceX began launching Starlink satellites, and as of September 2022 is reported to have launched more than 3,000 satellites into low-Earth orbit (LEO).
Businesses are Losing Big to Credential Stuffing Attacks
This week it was revealed that a huge credential stuffing attack had cost sports betting organization DraftKings $300,000. More specifically, cyber-crooks had used credential stuffing to gain access to many DraftKings customer accounts via a large-scale account takeover (ATO) attack and withdrawn funds. DraftKings has subsequently reimbursed the affected accounts, leaving the business out of pocket rather than its customers.
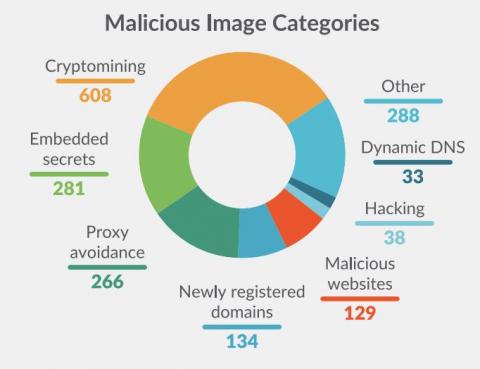
Analysis on Docker Hub malicious images: Attacks through public container images
Supply Chain attacks are not new, but this past year they received much more attention due to high profile vulnerabilities in popular dependencies. Generally, the focus has been on the dependency attack vector. This is when source code of a dependency or product is modified by a malicious actor in order to compromise anyone who uses it in their own software.
How Did LAUSD Get Hacked in 2022?
Vice Society, the cybercriminal gang responsible for the attack, is believed to have used internal login credentials leaked on the dark web to access LAUSD’s network and launch the ransomware attack. Twenty-three internal LAUSD credentials were leaked on the dark web leading up to the attack, with at least one set granting access to LAUSD’s Virtual Private Network (VPN).
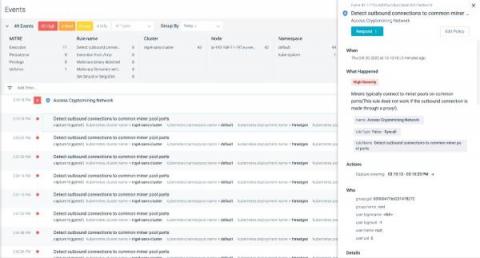
Detecting Cryptomining Attacks "in the Wild"
Cryptomining attacks are becoming more notable in-line with the rise of blockchain and cryptocurrencies, so detecting cryptomining has become a high priority. Security researchers have found data breaches related to various cryptominer binaries running within victims’ infrastructures. The default openness of Kubernetes clusters and the availability of the extensive compute power required for mining makes Kubernetes clusters a perfect target for cryptomining attacks.
Internal Reconnaissance Protection using NetCease and SAMRi10
Internal reconnaissance is one of the first steps an attacker will take once they have compromised a user or computer account in your network. Using various tools or scripts, they enumerate and collect information that will help them identify what assets they should try to compromise next to get what they want. For example, BloodHound will map out attack paths that can enable an adversary to escalate their privileges from ordinary user to admin.
The Top 5 Cyber Threats Facing Businesses Today
Businesses are more vulnerable to cybercrime now than ever before. Hackers are getting smarter and more sophisticated, and they are constantly coming up with new ways to exploit businesses online. If you want to protect your business from cybercrime, you need to be aware of the top 5 cyber threats that are facing businesses today. In this blog post, we will discuss each of these threats in detail and provide tips on how you can protect your business from them.
Russian-Speaking Threat Actors Claim New DDoS Attacks Against U.S. Targets
Citing senior Cybersecurity and Infrastructure Security Agency (CISA) officials, journalistsreported on November 8 that DDoS attacks had temporarily disabled the website of a state government. A group claiming to be pro-Russian hacktivists, CyberArmyofRussia_Reborn, claimed responsibility for that attack and another on the website of a U.S. political party’s governing body on the same day, specifying one target IP address for each organization.
How not to become a corporate account takeover victim 101
Account takeover is an attack where cybercriminals take ownership of user accounts using stolen credentials. It is essentially an identity theft fraud where the hacker, who now has full control over the user’s account, performs malicious activities posing as the real user. These malicious activities might include sending out phishing emails or messages, stealing and misusing sensitive financial or personal information, or using stolen information to takeover more user accounts.
How Patching Thwarts Cyber Attackers
The Real Cost of Cryptomining: Adversarial Analysis of TeamTNT
TeamTNT is a notorious cloud-targeting threat actor, who generates the majority of their criminal profits through cryptojacking. Sysdig TRT attributed more than $8,100 worth of cryptocurrency to TeamTNT, which was mined on stolen cloud infrastructure, costing the victims more than $430,000. The full impact of TeamTNT and similar entities is unknowable, but at $1 of profit for every $53 the victim is billed, the damage to cloud users is extensive.
Password attacks: How to combat them
“Treat your password like your toothbrush. Don’t let anybody else use it, and get a new one every six months.” – Clifford Stoll, Astronomer and engineer This identity security week, it’s important to understand the importance of passwords in cybersecurity, how easily they can be compromised if you are not careful, and how ManageEngine ADSelfService Plus helps fortify your passwords and enhance your organizational security.
The Simply Cyber Report: November 14, 2022
Common Payloads Attackers Plant in Malicious Software Packages
In this third post in our series on Malicious Software Packages, we’ll focus on the aftermath of a successful attack and how the attacker executes payloads to serve their needs through various real-life scenarios. Before we start, let’s review a few highlights from the second post you might’ve missed: Now, let’s get to blog three in the series.
More improvements to Attack Surface Custom Policies
In October, we launched a new feature called Attack Surface Custom Policies for Surface Monitoring customers. Attack Surface Custom Policies makes it possible to set, enforce, and scale customizable security policies so you can focus on the issues that matter most. Since launching this feature, we’ve generated thousands of alerts on potential risks for our customers. For some customers, it was particularly difficult to view these reports.
The Top 5 Cyber Threats 2022
Cyber Kill Chains Explained: Phases, Pros/Cons & Security Tactics
Sometimes referred to as CKC or the cyberattack lifecycle, the cyber kill chain is a security defense model developed to identify and stop sophisticated cyberattacks before they impact an organization. Typically comprised of seven steps, a cyber kill chain model breaks down the multiple stages of a cyberattack, allowing security teams to recognize, intercept or prevent them.
Development of the Ukrainian Cyber Counter-Offensive
Russia’s military incursion against Ukraine began on February 24, 2022, with a massive ground attack supported by several cyber incidents. This activity set the stage for what would become an active hybrid war fought in two domains: cyber and ground warfare.
New Phishing Technique Targeting Over 20 Crypto Wallets
Netskope Threat Labs spotted a new crypto-phishing attack that aims to steal sensitive data from crypto wallets, including private keys and security recovery phrases, disguising itself as a service to revoke stolen ERC (Ethereum Request for Comments) assets. The page was created and hosted with Netlify, which is a free cloud service to create websites and apps.
The Ultimate List of Biggest Bot Attacks Ever
Bots have been in the news a lot lately. Before committing to the Twitter takeover, Elon Musk cited huge bot numbers as a hurdle in completing the deal. Social media bots have also been blamed for interfering in elections and other political processes in recent years. Despite the current focus on bots, they’re not a new phenomenon. Bots have been around for decades — and some have caused serious damage to businesses around the world.
Detecting DOS attacks
Denial Of Service vulnerabilities
Cyber Attacks Are Coming, Cyber Security Must Ensure Business Survivability
NPM security: preventing supply chain attacks
NPM security has been a trending topic in the media in recent years, mostly in reference to npm packages available on the ecosystem rather than the npm registry itself. The increasing security risk, that applies to developers and software we build, makes it even more important to understand how to prevent supply chain attacks and other security vulnerabilities related to software development life cycle.
The Power of Manual Penetration Testing in Securing Your Attack Surface
When it comes to protecting software, don’t count on automated testing to find all the vulnerabilities in your code. Here’s why manual penetration testing is more essential (and more accessible) than one might think.
Remember, Remember: What Guy Fawkes and the Gunpowder Plot Can Teach Us About Modern Cyber Attacks
10 years ago I moved to the UK and made it my home, and I love living here. I like Marmite, debates over whether the evening meal is dinner, tea, or supper, the constant requirement to remark upon the weather… and the many bizarre traditions. One of these bizarre traditions is Bonfire Night, celebrated on 5th November each year to commemorate the Gunpowder Plot when a bunch of conspirators (including a man called Guy Fawkes) tried to blow up Parliament and King James.
Demystifying Breach Notification
As the number of high-profile cyberattacks and data breaches has increased in recent years, more companies have made investments to better secure their systems and develop incident response plans. While these are essential concerns, a firm’s obligations don’t simply end when a threat is removed from the network and they are able to resume normal operations. They must also notify those whose data may have been impacted by the breach.
KillNet Operations Against U.S. Targets Persist With Attempted Airport Website Attacks
In October, BleepingComputer reported that the websites of several airports were experiencing service disruptions after the KillNet threat actor group announced that they would target airports throughout the U.S.
The Top Cyber Attacks of October 2022
Responding to the Dropbox Breach with a Falco GitHub Plugin
On November 1st, Dropbox disclosed a security breach where the attackers stole over 130 code repositories after gaining access to one of the employee’s GitHub accounts using the stolen credentials of that employee via a well-designed phishing attack.
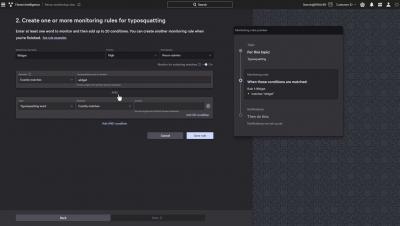
How to Protect Against Domain Impersonation with Falcon Intelligence Recon Typosquatting
DDoS Mitigation - Why Your Traditional Security Fails?
Under the Wing: Comm100 Supply Chain Attack
Hackers Stole Source Code From Dropbox
Read also: Vodafone Italy discloses a data breach, crypto exchange Deribit suffers a $28 million hack, and more.
Bed, Bath, and Beyond Struck by a Phishing Attack
Phishing hackers have struck again; this time, US retail brand, Bed, Bath & Beyond has fallen prey to the attack. Only a few details are available to the broader public; however, there is much more than meets the eye.
How to Protect Your Startup from Ransomware Attacks
As an entrepreneur, you're well aware of how devastating ransomware attacks can be. And as the frequency and magnitude of such attacks are constantly on the rise, devising a formidable plan to protect your startup from a ransomware attack is imperative. According to CrowdStrike 2022 Global Threat Report, there has been an 82% YoY increase in ransomware-related data leaks in 2021. What's more? According to Statista, there were 623.3 million ransomware attacks worldwide in 2021.
Linux security: How the third-most-used OS in the world has become the number one target of cyberattacks
AT&T Cybersecurity Insights Report: Focus Energy and Utilities
As energy and utilities companies strive to use the edge to innovate new solutions for delivering more efficient and resilient services, cybersecurity risks to carrying out those business missions loom large. Ransomware attackers and other cybercriminals have increasingly found energy and utilities organizations a profitable target, lobbying high-profile attacks in the last few years that have threatened safety and uptime in the process.
BYOD and Phishing Attacks: Top Threats Facing U.S. Government Organizations
Telework has become a mainstay, and with it, so has employee reliance on personal mobile devices. These devices are difficult to monitor and keep up to date, presenting a unique security challenge for U.S. local, state, and federal government organizations.
5 Biggest Supply Chain Attacks in 2022 (So Far)
Supply chain attacks have been on the rise in the last few years, rapidly becoming one of the most dangerous security threats. This article highlights some of the most noteworthy supply chain incidents observed in 2022.