Linux security: How the third-most-used OS in the world has become the number one target of cyberattacks
If we were to ask a bunch of people to choose a computer, they would most likely go with a Windows or Mac machine. The possibility of them choosing a Linux machine is slim. This is directly reflected in recent desktop adoption trends as well. Linux accounts for only 2.14% of all desktop operating systems (OSs) while its counterparts, Windows and Mac, occupy about 75.23% and 15.86% respectively.
The average population isn't looking for Linux as an OS; instead, this free, open-source software is widely adopted and used in a variety of fields ranging from smartphones to space missions. From powering over 400 million websites to having major names like Google, NASA, Intel, and Youtube among its clientele, Linux has gained a band of faithful users.
With more people experimenting with various Linux distros and learning about Linux's flexibility in solving their unique problems, the adoption rate is steadily increasing. Linux's market share is expected to grow at a CAGR of 19.2% between 2020 and 2027.
This rise in popularity has, however, put a target on Linux's back and it's showing. Linux malware was reported to be at an all-time high in the first half of 2022. In fact, September began with the news of a new Linux malware variant named Shikitega that was infecting computers and IoT devices and was bypassing detection. The total number of vulnerabilities detected year-over-year shows that after Microsoft and Apple, it's Linux distros like RedHat and Debian that have the highest numbers of vulnerabilities reported.
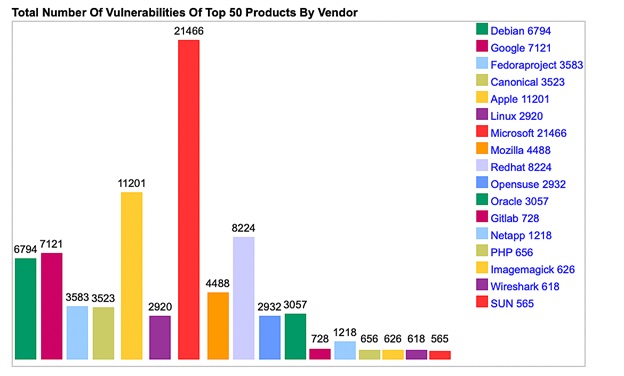
Image source: https://www.cvedetails.com/top-50-products.php
Enterprises are slow to react to Linux vulnerabilities for a variety of reasons, including:
- The absence of proper patch management workflows or software to deal with Linux vulnerabilities.
- A negligible number of machines running Linux OSs.
- Limited third-party application support for Linux machines.
- The manual work involved in setting up policies and restrictions for Linux systems.
With the increasing attacks against Linux distros, it's important to know and follow certain security measures to safeguard your Linux systems against cyberattacks. Here are a few tips that are easy to do and will kick-start your Linux security approach.
Regular software audits: This rule isn't unique to Linux systems. As part of maintaining good cyberhygiene, it's important to regularly audit the software that's running in your network and uninstall software that is outdated or not needed. Less software means fewer vulnerabilities.
Linux security extensions: You can use Linux security software like SELinux, AppArmor, and grsecurity to enforce restrictions and access controls. These extensions can be used to enforce network-level and program-level restrictions. SELinux especially is a must have—if you're using Linux, make sure it's enabled. You can view it's status by running any of the following commands:
system-config-selinux
getenforce
sestatus
Password policies: Properly maintain Linux user accounts. You can use commands like useradd and usermod to create and maintain accounts. Make sure your passwords are strong. Configure password expiration policies to mandate password changes after a set number of days.
Check the permissions of non-root accounts: Only root accounts have full access to the system and have a unique identifier (UID) set to 0. Check to see if there are other accounts that have a UID set to 0 and delete them. You can use the following command to check for root accounts:
# awk -F: '($3 == "0") {print}' /etc/passwd
Turn off IPv6 when not used: Check if your applications are using IPv6. If not, it's best to disable it, because most Linux policies do not require IPv6. You can use the following commands for disabling IPv6 in the following distros:
- Red Hat, CentOS, and Fedora:
- Open the conf file.
- Add # vi /etc/modprobe.conf.
- Then add alias net-pf-10 off.
- Save the file and then close it.
- Reboot your system.
- Debian and Ubuntu:
- Open the /etc/modprobe.d/aliases
- Find the alias net-pf-10 ipv6
- Replace it with alias net-pf-10 off alias ipv6 off.
Encrypt communication and use Secure Shell (SSH): One of the best practices to follow is to encrypt data that is transmitted. Replace Telnet and rlogin protocols that use plain text with SSH protocol that uses encryption. You can also change the default port and enforce the following restrictions by running the # vi /etc/ssh/sshd_config command and, in the file that opens, entering the relevant commands:
- Disabling root login:PermitRootLogin no
- Allowing specific users:AllowUsers username
- Using SSH protocol version 2:Protocol 2
Back up files regularly: This is the golden rule for any and all enterprise data regardless of the OS. Perform differential backup at regular intervals and store the backup in secure locations. You can also opt for traditional UNIX backup methods like dump and restore.
Update Linux kernel and software: The best way to prevent cybercrimes is to keep your Linux kernel and software up to date. Deploy the latest updates available for Linux distros. Many software solutions that help automate patch management don't support Linux because of it's smaller user base. With the increase in threats to Linux distros, it's essential to have a solution that will take care of automatically detecting the updates needed for Linux systems and deploying them to the relevant systems.
ManageEngine Patch Manager Plus provides active support for most prominent Linux distros. With support for Red Hat, Ubuntu, SUSE Linux, Pardus, Oracle Linux, Debian, and CentOS, you can automatically detect and deploy missing updates to the respective systems.
Patch Manager Plus uses the following workflow for Linux patch management:
- Scanning for patches at regular intervals - Patch Manager Plus regularly syncs with the central patch repository, scans its managed endpoints for missing patches based on the latest patch information in the repository.
- Automatic testing and approval of patches - Once the missing patches are identified, these patches can be configured to be deployed to a pilot group of systems (Test group). This testing makes sure that the updates are compatible with the applications running in the production environment and won't misbehave. Successfully tested updates are approved automatically and can be pushed out to the production machines.
- Enforcing deployment policies and offering flexible, customizable deployment options - Regular patch management should not hinder productivity. With Patch Manager Plus' vast range of customizability, you can set the deployment to occur at a time and window of your convenience.
- Automating patch deployment - Set tasks to automatically start executing every time there is a missing patch detected in your Linux systems. Automation is the key to keeping your systems regularly updated.
- Offering comprehensive reports - You can't manage what you can't measure. Patch Manager Plus returns detailed reports on the status of the systems in your network, the status of patch deployment, and everything else you need to know in order to curate the perfect patch routine. You can also export these reports and maintain them for auditing purposes.
Following these best practices and setting up an automated update process for your Linux systems could simplify your security process to a large extent and keep your systems airtight. Start a free, 30-day trial of Patch Manager Plus to experience seamless Linux patch management for yourself.

