Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Despite a Majority of Organizations Believing They're Prepared for Cyber Attacks, Half Were Still Victims
A new survey points to an overconfidence around organization’s preparedness, despite admitting to falling victim to ransomware attacks – in some cases multiple times. According to Fortinet’s 2023 Global Ransomware Report, the threat of ransomware at face value seems to be of high importance to organizations: But the data also shows that despite the focus on protecting against attacks and believing they are ready, organizations still fell victim.
What is a Cyberattack?
A cyberattack is an attack on computers, networks or systems by cybercriminals in an attempt to steal or access sensitive information. The information stolen during an attack can also open the door to other types of cyberattacks such as social engineering scams. Continue reading to learn more about cyberattacks and what you can do to protect yourself against them, both in your personal life and at your workplace.
Charming Kitten targets critical infrastructure in US and elsewhere with BellaCiao malware
Iranian state-sponsored hacking group Charming Kitten has been named as the group responsible for a new wave of attacks targeting critical infrastructure in the United States and elsewhere.
Evolving cyberattack landscape: What to expect in the future
In today’s increasingly digitized world, cybersecurity has become an essential concern for individuals and businesses alike. With more and more data being transmitted and stored online, the risk of cyberattacks and data breaches has never been higher. The field of cybersecurity is rapidly growing and evolving, with new technologies emerging all the time.
Preventing Cross-Site Scripting (XSS) in Java applications with Snyk Code
Java is a powerful backend programming language that can also be used to write HTML pages for web applications. However, developers must know the potential security risks associated with Cross-Site Scripting (XSS) attacks when creating these pages. With the rise of modern templating frameworks, preventing security attacks through proper input validation and encoding techniques has become easier.
SLP: a new DDoS amplification vector in the wild
Earlier today, April 25, 2023, researchers Pedro Umbelino at Bitsight and Marco Lux at Curesec published their discovery of CVE-2023-29552, a new DDoS reflection/amplification attack vector leveraging the SLP protocol. If you are a Cloudflare customer, your services are already protected from this new attack vector.
Mitigating rogue devices with OpUtils: What you need to know
Over the past few years, IT companies adopted IoT, wireless and hybrid networks to stay competitive and to meet the demands of their clients. Among these networks, wireless networks are the most common and the most vulnerable to cyberattacks as hackers constantly try to penetrate them. A cyberattack is initiated by planting a rogue device in your organization’s network.
The Weak Link: Recent Supply Chain Attacks Examined
Software Supply Chain Security at RSA Conference 2023
The risk of supply chain attacks increases as more companies rely on third-party vendors and suppliers for critical services and products. Supply chain attacks have become increasingly prominent in recent years. In 2022, for instance, supply chain attacks surpassed the number of malware-based attacks by 40%.
Under the Wing: Protecting Small Businesses Against Big Attacks
CyberTalk with Bill and Robin - 20th April 2023
11:11 Systems' CTO shares insight into Oakland's ransomware attack
How Social Engineers Collect Data to Build an Attack
How Many Cyber Attacks Per Day: The Latest Stats and Impacts in 2023
As we gear up to enter the new financial year, one thing is for sure: cyberattacks per day continue to pose a major threat to businesses of all sizes. With the rise of IoT attacks and the low prosecution rate of cybercriminals, it’s no wonder that companies are spending billions to protect themselves.
Healthcare Cyber Attack Statistics
As technology has advanced and the world has become more interconnected, the threat of cyber-attacks has become a significant concern for businesses, smaller healthcare organisations, governments, civil rights and individuals alike. While cyber-attacks can target any sector, healthcare organisations have become an increasingly attractive target for cybercriminals in recent years.
Small business cyber attack statistics including surprises for 2023
A cyber attack or data breach is a threat to every business. Still, it can be more devastating for small businesses as they face numerous challenges, including cash inflow, competition, employee retention, limited funding, supply chain and other business problems simultaneously, making it difficult for them to survive.
Microsoft warns accounting firms of targeted attacks as Tax Day approaches
Accountants are being warned to be on their guard from malicious hackers, as cybercriminals exploit the rush to prepare tax returns for clients before the deadline of US Tax Day. US Tax Day, which falls on Tuesday April 18 this year, is the day on which income tax returns for individuals are due to be submitted to the government. Inevitably it's a busy time for accounting firms and bookkeepers who are feverishly collecting necessary documents from their clients.
Key Takeaways from S&P Global Market Intelligence Discovery Report: The Impact of Continuous Security Validation
In late 2022, SafeBreach commissioned S&P Global Market Intelligence to conduct a research project surveying 400 highly qualified security practitioners across the United States and Europe. The goal was to understand respondents’ biggest security challenges, the level of adoption and maturity of the continuous security validation (CSV) tools they use to address those challenges, and the business outcomes they achieved.
Vow to safeguard digital identities from cyberattacks this Identity Management Day
As our lives become more intertwined with the digital world, cyberattacks are growing in sophistication. And since the pandemic, the prevalence of hybrid work culture has posed additional security challenges. This creates pressure for businesses to implement advanced measures to safeguard their users’ digital identities and network resources. Failing to do so not only damages an organization’s reputation, but also leads to numerous legal issues and heavy recovery costs.
Malicious Packages Special Report Reveals 315% Spike in Attacks
Today’s attackers aren’t just exploiting vulnerabilities — research from Malicious Packages Special Report: Attacks Move Beyond Vulnerabilities illustrates the growing threat of malicious packages. According to the report, the number of malicious packages published to npm and rubygems alone grew 315 percent from 2021 to 2022.
DDoS threat report for 2023 Q1
Welcome to the first DDoS threat report of 2023. DDoS attacks, or distributed denial-of-service attacks, are a type of cyber attack that aim to overwhelm Internet services such as websites with more traffic than they can handle, in order to disrupt them and make them unavailable to legitimate users. In this report, we cover the latest insights and trends about the DDoS attack landscape as we observed across our global network.
The Credential Stuffing Guide: How To See & Stop Credential Stuffing Attacks
Recent Cyber Attacks - 2023
The prediction is that $8 trillion will be lost to cyber crimes by the end of 2023, which is almost a third of the USA’s GDP in 2022 and twice as much as India’s predicted GDP in March 2023. The global loss to cybercrime is will grow more than 15% year by year to reach $10.5 trillion by 2025.
What is a Cross-Site Request Forgery (CSRF) Attack?
Successful hackers have the ability to find a specific vulnerability and turn it into millions of dollars if the account is large enough. Good hackers keep it simple by using the browser as a means to attack unwitting users. Cross-site request forgery, commonly called CSRF, is an innovative attack method in which hackers use header and form data to exploit the trust a website has in a user’s browser.
What Is a DMA Attack? Understanding and Mitigating the Threat
You have probably wondered what would happen if your company laptop got lost or stolen. Would someone be able to extract sensitive data from your laptop even if the device is encrypted or locked? There are several ways to compromise a laptop with physical access, and one of them is through a direct memory access (DMA) attack.
Protecting Nonprofits From Cyber Attacks
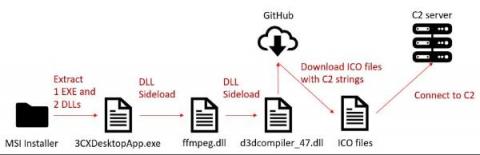
How to Detect and Mitigate the 3CXDesktopApp Supply Chain Attack
On March 29, researchers from two security companies identified an active campaign originating from a modified version of a legitimate, signed application: 3CXDesktopApp, a popular voice and video conferencing software. 3CXDesktopApp is developed by 3CX, a business communications software company. According to its website, 3CX has 600,000 client organizations and 12 million daily users.
SQL INJECTION ATTACK
The New Frontiers of Cybersecurity - Exponential Increase in Complexity
The New Frontiers of Cybersecurity is a three-part thought-leadership series investigating the big-picture problems within the cybersecurity industry. In the first post, we explored the reasons malicious actors have been able to enhance their ability to execute and profit from attacks. In the second post, we discussed how the massive increase in endpoints and systems online has dramatically increased the attack surface.
NCB Management Services Hit By a Cyber Attack Exposing Data for 500,000 Consumers
NCB Management Services is a debt-buying company that acquires debt from other businesses and attempts to collect that debt. The organization works with many major companies, such as Bank of America, and it suffered from a serious data breach recently. Since NCB works with so many major companies, customers of those companies can be put at risk of data loss when their data is lost.
A State of Siege: Cyberattacks Soar Across the UK and Ireland
Organisations across the UK and Ireland must take precautions to protect their systems to reduce their risk of cyberattack.
Chinese fraudsters: evading detection and monetizing stolen credit card information
Cyber attacks are common occurrences that often make headlines, but the leakage of personal information, particularly credit card data, can have severe consequences for individuals. It is essential to understand the techniques employed by cyber criminals to steal this sensitive information.
Proxyjacking has Entered the Chat
Did you know that you can effortlessly make a small passive income by simply letting an application run on your home computers and mobile phones? It lets others (who pay a fee to a proxy service provider) borrow your Internet Protocol (IP) address for things like watching a YouTube video that isn’t available in their region, conducting unrestricted web scraping and surfing, or browsing dubious websites without attributing the activity to their own IP.
The Top Cyber Attacks of March 2023
Mid-Sized Businesses Lack the Staffing, Expertise, and Resources to Defend Against Cyberattacks
Mid-sized businesses – those with 250 to 2000 employees – don’t appear to have what they need to fend off attacks in a number of critical ways. Cybersecurity vendor Huntress’ latest report, The State of Cybersecurity for Mid-Sized Businesses in 2023, shows that mid-sized businesses are in a heap of trouble and simply aren’t prepared for an attack: In short, organizations have no internal resources to ensure the organization is improving its state of cybersecurity daily.
TMX Finance Suffers a Cyber Breach, and Customer Data is Exposed
TMX Finance is a large financial company that specializes in short-term loans for in-need individuals. The company has been in operation since 1998 and runs businesses like InstaLoan, TitleMax, and TitleBucks. The organization maintains more than 900 locations in 14 separate states and employs more than 2,000 individuals overall. This large finance company recently suffered from a cyber attack that exposed some of its customers in a serious way.