Shamane Tan on cyber resilience - Cyber Security Decoded
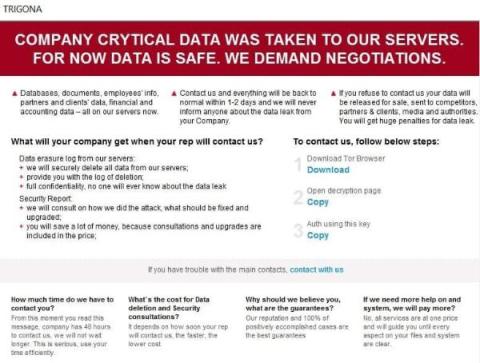
Bouncing back from a cyber incident, data breach or #ransomware attack is a great accomplishment…but how can you bounce forward? A complete Cyber Resilience strategy is mission-critical. Security teams should be proactive and have response plans in place for when #CyberAttacks hit, rather than attempting to prevent attacks from occurring. With a #CyberResilience strategy, your team will be equipped with a plan when a cyber incident occurs while also having tools to identify those malicious attacks before they happen.