|
By Jamison Utter
As organizations race to adopt the latest advancements in artificial intelligence, DeepSeek serves as a cautionary tale about the potential dangers of rushing into the hype cycle without adequate consideration of security and ethical implications. DeepSeek, a Chinese AI startup, has been identified as having several significant security risks and vulnerabilities that could pose threats to both the company and its users.
|
By A10 Staff
A cloud transformation is no time to discover shortcomings in your load balancing solution—or the vendor who provides it. But according to a recent series of industry surveys, that’s exactly the situation currently facing many enterprises. With hybrid environments now the norm, and cloud-first strategies on the agenda, both load balancer/ADC functionality and vendor relationships are leaving IT leaders unsatisfied. And that’s enough to make them consider other options.
|
By Akhilesh Dhawan
In today’s digital age, as organizations modernize their applications and infrastructure by embracing hybrid cloud environments, API-centric architectures, and AI-driven technologies to enhance customer experiences and productivity, they also face an unprecedented increase in cyber threats aimed at disrupting their operations.
|
By Akhilesh Dhawan
Building AI and LLM inference and integrating it in your environment are major initiatives, and for many organizations, the most significant undertaking since cloud migration. As such, it’s crucial to begin the journey with a full understanding of the decisions to be made, the challenges to overcome, and the pitfalls to be avoided along the way.
|
By A10 Staff
Application delivery has never been more critical—or more challenging. Customers, partners, and employees expect a great experience every time they access your apps, without having to worry about the security of their data. But meeting that expectation gets harder every day, as complex hybrid and multi-cloud environments, intensifying threats, rising scale, and constantly changing business requirements put new demands on your infrastructure.
|
By Mikko Disini
For most enterprises, the question isn’t whether to use AI—it’s where and how. For customers, AI enables more personalized experiences and faster response times. Employees can achieve higher productivity with more intuitive ways of working. Businesses can open new revenue streams and build competitive differentiation while strengthening security. The potential benefits are many—but realizing them isn’t a trivial matter.
|
By Nick Bond
The EU’s Network and Information Systems Directive 2 (NIS2) for cybersecurity resilience entered full enforcement in October 2024, and compliance with its requirements presents major challenges for many companies, particularly those in the financial services sector. And while most IT leaders are confident of achieving NIS2 compliance, they also acknowledge that this cybersecurity directive has exacerbated existing challenges such as resource constraints and skills gaps.
|
By Jamison Utter
In the digital age, distributed denial of service (DDoS) attacks pose a significant threat to organizations, potentially leading to service disruptions and financial losses. To effectively combat these threats, businesses are increasingly adopting hybrid DDoS protection solutions. By integrating cloud traffic scrubbing, on-premises local protection, global DDoS-specific threat intelligence, and an orchestration platform, hybrid solutions offer a comprehensive defense strategy.
|
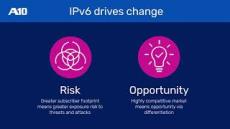
By Mark Dixon
It is hard to believe that World IPv6 Launch Day was 12 years ago on 6 June 2012, and while worldwide adoption of IPv6 continues to accelerate, uptake has not been as fast as anticipated. The purpose of the World IPv6 Launch Day was to encourage service providers and web companies to test their services and evaluate their capabilities in the face of the global exhaustion of IPv4 addresses.
|
By Jamison Utter
In the digital era, websites are increasingly vulnerable to a variety of automated threats. These threats, executed by malicious bots, can lead to significant financial losses, data breaches, and compromised user experiences. To safeguard against these risks, it is imperative for websites to implement robust bot protection.
|
By A10 Networks
The European Union is tackling systemic risk in critical digital systems with two new regulations that come into force in the next 12 months. Watch to understand how to ensure your company's compliance with NIS2 and DORA regulations with the help of A10 Networks.
|
By A10 Networks
A10 Defend Threat Control provides a robust first layer of DDoS defense. By leveraging proprietary ML/AL-enhanced data processing techniques, Threat Control proactively monitors attackers and understands key DDoS attack methods, with or without dedicated DDoS prevention solutions.
|
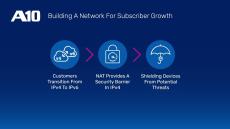
By A10 Networks
The transition from IPv4 to IPv6 won't happen overnight—but it doesn't have to be an ongoing headache. Learn how you can bridge the shift from IPv4 to IPv6 with a lifecycle strategy that meets both short-term needs and long-term requirements for your customers, subscribers and business.
|
By A10 Networks
As the world experiences uncertainty stemming from economic, social, and geopolitical disruption, digital connectivity has never been more important to address inequality, support communities and drive global business recovery. This survey interviewed 2,750 communication service provider IT professionals. Respondents come from a broad range of provider types, data center/co-location, service providers and fixed wireless access providers.
|
By A10 Networks
A10 Next-Gen WAF, powered by Fastly, leverages advanced technology to protect web applications from complex modern threats while minimizing false positives and ensuring availability. See how our integrated Next-Gen WAF, enabled on Thunder ADC, effectively blocks attacks while remaining user-friendly. Get insights into its visibility, DevOps, security tool integrations, and analytics features for advanced web application protection.
|
By A10 Networks
The term of the day is DDoS-for-hire, a service that allows anyone to purchase and carry out a distributed denial of service (DDoS) attack. This type of service is modeled after the Software as a service (SaaS) business model and is often profitable because it allows the operator of an Internet of Things (IoT) botnet to conduct a cost-effective attack.
|
By A10 Networks
Today's term is cipher suite, a combination of algorithms that are used in cryptography to secure communication between servers and clients. A cipher suite includes a series of ciphers that fulfill various purposes, such as key generation, authorization, and integrity checksumming. These ciphers ensure the confidentiality and authenticity of the information being transmitted by encrypting and decrypting it. The client and web server negotiate and agree on the specific cipher suite to be used for their communication.
|
By A10 Networks
Today we'll be discussing CGNAT, or Carrier-Grade Network Address Translation. This technology was created to address the finite number of public IP addresses that were available under the IPv4 protocol. In the 1980s, it was anticipated that each computer would have its own unique public IP address, but the total number of addresses available, 4 billion, eventually ran out. As a result, IPv6 was developed to address the limited address space of IPv4, but it is not backwards compatible.
|
By A10 Networks
Navigating the digital landscape can present performance and security challenges. Interruptions caused by jitter and downtime can negatively impact the performance of your applications. Additionally, modern cyber threats, including DDoS attacks and encrypted malware, can compromise data and disrupt operations.
|
By A10 Networks
Domain Name System (DNS), often referred to as the "phonebook of the internet," is an important protocol for the overall functioning of the internet, translating domain names into IP addresses and vice-versa. DNS, though, is an inherently insecure protocol and is vulnerable to a variety of cyberattacks that can disrupt network and service availability and violate confidentiality of users and their data. This poses a challenge for the teams responsible for ensuring uninterrupted DNS service and maintaining user privacy.
|
By A10 Networks
Secure application delivery in a hybrid cloud environment is the foundation of modern digital business-but it also poses significant challenges. There's more than one way to go hybrid cloud. To meet the challenges of a hybrid cloud environment, many organizations are now adopting a cloud operating model. The goal is to use technology to create a secure, flexible, scalable, and agile IT infrastructure that can support business growth and innovation while optimizing cost efficiency. But achieving these goals can be a challenge.
SDxCentral Solution Guide: How to Ensure Effective and Secure Application Delivery in a Hybrid Cloud
|
By A10 Networks
Enterprises have been moving to hybrid cloud environments for years, whether for cost savings, data sovereignty, or geographic reasons. As IT environments grow increasingly complex, and security and compliance continue to present new challenges, many organizations are looking for a more effective approach to application delivery.
|
By A10 Networks
A Zero Trust Approach to Protect Data Privacy Data protection in healthcare is critical. From the hospitals at the front line, to the insurance providers behind the scenes, all such organizations bear the dual responsibility of protecting themselves, as well as their patients. They must safeguard their data privacy, identity, security, and finances of their patients. They must also protect their own organization from costly breaches, regulatory fines, and damage to their business, reputation, and patient relationships.
|
By A10 Networks
Not that long ago, organizations were squarely focused on moving their applications and infrastructure to the cloud to benefit from its scalability, flexibility, and cost savings. Today, however, priorities are shifting, leading many to focus on right-sizing hybrid cloud deployments and establishing digital resilience. You will learn how digital resilience for hybrid cloud application delivery.
- February 2025 (3)
- January 2025 (1)
- December 2024 (1)
- November 2024 (5)
- October 2024 (3)
- September 2024 (3)
- July 2024 (3)
- June 2024 (2)
- May 2024 (1)
- April 2024 (1)
- March 2024 (4)
- February 2024 (5)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (1)
- August 2023 (4)
- June 2023 (2)
- May 2023 (1)
- April 2023 (1)
- January 2023 (12)
A10 Networks provides security and infrastructure solutions for on-premises, hybrid cloud, and edge-cloud environments. Our 7000+ customers span global large enterprises and communications, cloud and web service providers who must ensure business-critical applications and networks are secure, available, and efficient.
Why Customers Choose A10:
- Industry-leading Performance: Fastest response and lowest latency for mission-critical applications.
- Comprehensive and Integrated Security: Including options for next-gen WAF, DNS application firewall along with integrated DDoS protection.
- Simple Operations for Predictable OPEX: With all-inclusive license and flexible scale-out across multi or hybrid clouds.
- World-class Customer Support: With available and committed team for support when you need it.
Eliminate Costly Downtime, and Risk of Revenue Loss.