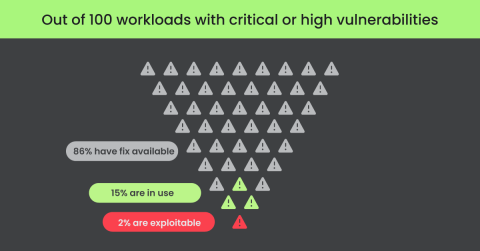
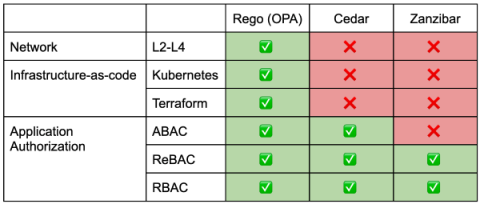
Cloudflare acquires BastionZero to add Zero Trust infrastructure access controls for Cloudflare One, the world's largest Secure Access Service Edge (SASE) network
Acquisition adds secure remote infrastructure access to Cloudflare One, safeguarding customers' most critical systems.