Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Application Security
The latest News and Information on Application Security including monitoring, testing, and open source.
Best practices for application security in cloud-native environments
Editor’s note: This is Part 3 of a five-part cloud security series that covers protecting an organization’s network perimeter, endpoints, application code, sensitive data, and service and user accounts from threats. In Parts 1 and 2 of this series, we discussed the importance of protecting the boundaries of networks in cloud environments and best practices for applying efficient security controls to endpoints.
The Risks and Benefits of Updating Dependencies
One of the most important steps of securing your code base, your software, and your applications, is to update the dependencies they rely on. In principle, maintaining software health with updates demands that you use recent versions of any software and dependencies. Recent updates are less likely to be exploited and attacked via publicly known vulnerabilities than older versions, because with the latter, malicious actors have had more time to hunt for weaknesses.
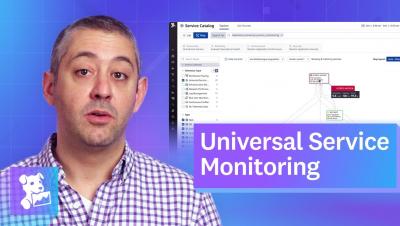
This Month in Datadog: Cloud SIEM Investigator, API Catalog, Expanded AWS Coverage, and more
OpenAI (ChatGPT) Vulnerability Remediation Concept Work
In Modern AppSec, DevSecOps Demands Cultural Change
This is the final of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. When thinking of adjectives to describe cyberattackers, it’s doubtful that many people would choose to call them innovative – a term we’re more likely to ascribe to things we enjoy. But the reality is that adversaries are innovative, constantly finding new ways to launch attacks that result in greater rewards for less effort.