How To Do AppSec: The Application Security Guide
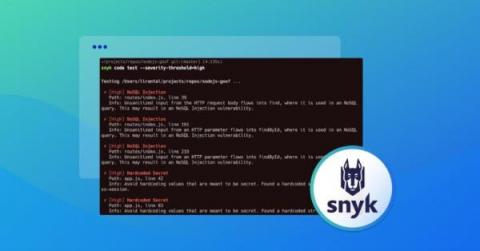
Modern applications are sophisticated, with different third-party software and hardware components and complicated integrations compared to legacy applications. With these complications, there is an increase in exploitable vulnerabilities in the application layer. Thus, application security is one of the most critical aspects organizations should focus on to secure their applications from cyberattacks.