Reflective DLL Injection In The Wild
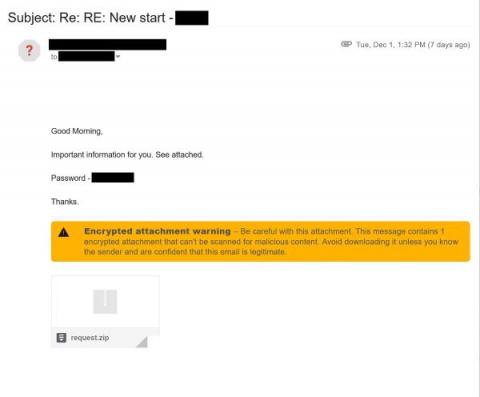
December 2020, the weeks before Christmas, saw an increase in reported malware activity that culminated most prominently in the Sunburst Trojan attacks - events that are still developing as of today. As we were asserting our readiness to respond to new threats under our watch, we identified a suspicious executable being copied to a remote network share.