Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
August 2023
Threat-Loaded: Malicious PDFs Never Go Out of Style
In the realm of cybersecurity, danger hides where we least expect it and threats never, ever, go out of style! Over the past few months, Trustwave SpiderLabs has seen a rising trend in threat actors employing PDF documents to gain initial access through email-borne attacks. Though the use of PDF files as a malicious vector is not a novel approach, it has become more popular as threat actors continue to experiment with techniques to bypass conventional security controls.
Ongoing Ransomware Campaign Against Cisco ASA VPN Appliances
Coffee Talk with SURGe: 2023-SEPT-05 Mudge Joins CISA, Qakbot Takedown, Infamous Chisel Malware
JUMPSEC research reveals ransomware attacks rising again
1H 2023 Ransomware Landscape Overview
Harnessing the Power of Rubrik Security Cloud (RSC) Integration with ServiceNow: A Strategic Leap in Data Management
With the goal of achieving robust and efficient data management, one cannot overlook the prowess of Rubrik Secure Cloud (RSC), a platform encapsulating a comprehensive suite of GraphQl APIs. As many organizations trust both Rubrik and ServiceNow for their operational needs, blending these two systems creates a potent synergy.
Battling malware in the industrial supply chain
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Rubrik Cyber Recovery Named Gold Winner at VMware Explore 2023
Las Vegas was buzzing last week with VMware Explore where Rubrik Cyber Recovery snagged the top award in the Business Continuity and Data Protection category. Our excitement continued when Rubrik Data Threat Analytics earned an honorable mention in the Security, Networking, and Edge category!
CTI Roundup: An XLoader macOS variant, Lazarus Group Update, and Hackers Abuse Facebook Ads
XLoader macOS variant poses as a productivity app, Lazarus Group uses new malware, and threat actors abuse Facebook promotions to spread malicious code.
The Windows Restart Manager: How It Works and How It Can Be Hijacked, Part 1
Malware utilizes a multitude of techniques to avoid detection, and threat actors are continuously uncovering and exploiting new methods of attack. One of the less common techniques includes the exploitation of the Windows Restart Manager. To stay ahead of malicious authors, it is important to be aware of them and understand how they work.
CTI Roundup: Monti ransomware targets VMware ESXi servers with new Linux locker
Raccoon Stealer malware reappears, AI adoption remains low among threat actors, and Monti ransomware targets VMware ESXi servers with new Linux locker.
What Is Ransomware: Internet Survival Strategies
Akira Ransomware, 8Base Ransomware, and more: Hacker's Playbook Threat Coverage Round-up: August 22, 2023
In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting newly added coverage for several recently discovered or analyzed ransomware and malware variants, including Akira ransomware, 8base ransomware, and Rorschach (BabLock) ransomware, amongst others. SafeBreach customers can select and run these attacks and more from the SafeBreach Hacker’s Playbook™ to ensure coverage against these advanced threats.
Transforming Uncertainty into Certainty: Introducing Rubrik AI-Powered Cyber Recovery
Today, cyberattacks pose the most significant threat to an organization’s data. The Spring 2023 Rubrik Zero Labs report, based on research from over 1,600 IT and Security professionals, revealed that 99% of IT and security leaders were informed of at least one attack in their own environment in 2022.
Prioritizing cyber resilience in response to a potential ransom payment ban
Ransomware attacks do not simply start and end with a locked computer screen and a ransom note. They unravel as intricate narratives, leaving a trail of financial wreckage, operational interruptions, and reputational damage in their wake. These attacks bear significant costs. In 2022, the average cost of a ransomware attack was a whopping $4.54 million, per IBM Security and the Ponemon Institute. And that does not include the actual ransom payment itself.
LABRAT: Stealthy Cryptojacking and Proxyjacking Campaign Targeting GitLab
The Sysdig Threat Research Team (TRT) recently discovered a new, financially motivated operation, dubbed LABRAT. This operation set itself apart from others due to the attacker’s emphasis on stealth and defense evasion in their attacks. It is common to see attackers utilize scripts as their malware because they are simpler to create. However, this attacker chose to use undetected compiled binaries, written in Go and.NET, which allowed the attacker to hide more effectively.
Rhysida Ransomware - Detecting a Significant Threat to Healthcare and Other Sectors
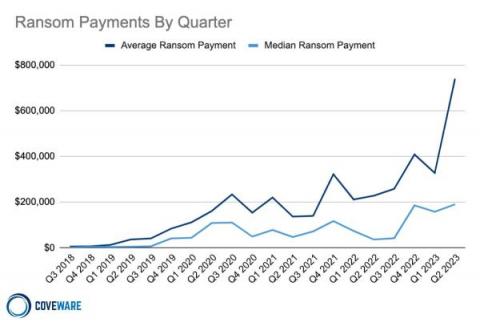
Ransomware's Paradox: Why Falling Monetization Rates Are Accompanied by Soaring Ransom Payments - A Must-Read Analysis.
Grab a cup of coffee, and let's talk about something that's been making waves in the cybersecurity world: ransomware. You've probably heard about the alarming rise in ransom payments, but did you know that ransom monetization rates have actually fallen to a record low? It's a complex and evolving landscape, and we're here to break down the recent very interesting Coveware report for you.
Ransomware Attacks Surge as Generative AI Becomes a Commodity Tool in the Threat Actor's Arsenal
According to a new report, cybercriminals are making full use of AI to create more convincing phishing emails, generating malware, and more to increase the chances of ransomware attack success. I remember when the news of ChatGPT hit social media – it was everywhere. And, quickly, there were incredible amounts of content providing insight into how to make use of the AI tool to make money.
CTI Roundup: Rhysida Ransomware Threatens the Healthcare Sector
Cloud takeover campaign targets top-level executives, Rhysida ransomware threatens the healthcare sector, and LOLKEK ransomware continues to evolve.
Stories from the SOC - Unveiling the stealthy tactics of Aukill malware
On April 21st, 2023, AT&T Managed Extended Detection and Response (MXDR) investigated an attempted ransomware attack on one of our clients, a home improvement business. The investigation revealed the attacker used AuKill malware on the client's print server to disable the server's installed EDR solution, SentinelOne, by brute forcing an administrator account and downgrading a driver to a vulnerable version.
ProxyNation: The dark nexus between proxy apps and malware
AT&T Alien Labs researchers recently discovered a massive campaign of threats delivering a proxy server application to Windows machines. A company is charging for proxy service on traffic that goes through those machines. This is a continuation of research described in our blog on Mac systems turned into proxy exit nodes by AdLoad.
What Is Malvertising?
Malvertising–also called malicious advertising–is when cybercriminals use advertisements to infect devices with malware. Malvertising can appear on any advertisement you see online, you don’t necessarily have to be on a malicious website to be a victim of this cyberthreat. When a victim is exposed to a malvertisement, their device and data are at risk of being compromised, even if they don’t interact with the advertisement.
Gootloader Malware Uses Social Engineering to Target Law Firms (or their Clients)
Law firms are being targeted by a large number of social engineering attacks involving the Gootloader malware delivery tool, according to researchers at Trustwave. “Recently, we’ve seen a noticeable surge in malware cases linked to a malicious payload delivery system known as Gootloader,” the researchers write. “The group behind this malware is believed to operate a malware-as-a-service operation, exclusively providing a malware delivery service for other threat actors.
Number of Named Ransomware Victim Organizations Jumps 64% in One Quarter
The second quarter of this year has become the focus of some new firsts in ransomware attacks, according to new data from cybersecurity vendor Reliaquest. None of us want to see ransomware continue “up and to the right” on a chart. But it appears that this is the case, according to Reliaquest’s Ransomware Report: Q2 2023.
Rhysida ransomware - what you need to know
Rhysida is a Windows-based ransomware operation that has come to prominence since May 2023, after being linked to a series of high profile cyber attacks in Western Europe, North and South America, and Australia. The group appears to have links to the notorious Vice Society ransomware gang.
Mac systems turned into proxy exit nodes by AdLoad
AdLoad malware is still infecting Mac systems years after its first appearance in 2017. AdLoad, a package bundler, has been observed delivering a wide range of payloads throughout its existence. During AT&T Alien Labs’ investigation of its most recent payload, it was discovered that the most common component dropped by AdLoad during the past year has been a proxy application turning MacOS AdLoad victims into a giant, residential proxy botnet.
One Drive, Double Agent: Clouded OneDrive Turns Sides
Over the past few years, ransomware has emerged as one of the most significant cybersecurity threats. Recent research conducted by Sophos indicates that the situation is becoming increasingly dire. Notably, the payments demanded by ransomware groups have surged, making the attacks even more costly for victims. Additionally, an alarming 66% of organizations have reported being targeted by ransomware attacks in the last two years alone.
There's a New Stealer Variant in Town, and It's Using Electron to Stay Fully Undetected
Our threat research team recently uncovered new npm packages that are used to download a new info-stealer variant that uses the popular Electron framework to disguise itself as a legitimate application. In this blog post, we’ll analyze the attack flow of this new info-stealer we detected and explain how it can stay undetected by abusing trusted development tools like Electron.
.NET developers alert: Moq NuGET package exfiltrates user emails from git
On August 8, 2023, the.NET community was informed that the testing library called Moq exfiltrates developer's emails from their development machine and sends them off to third-party remote servers. Snyk has already published a security advisory and will alert developers who scan and monitor their.NET projects with Snyk.
Four Consecutive Years as Both a Leader and Furthest in Vision in the 2023 Gartner Magic Quadrant for Enterprise Backup and Recovery Software Solutions
Rubrik is on a mission to secure the world’s data, and our position as an innovator has been reaffirmed in this 4th consecutive year being a Leader and furthest on Vision in the 2023 Gartner Magic Quadrant for Enterprise Backup and Recovery Solutions. This recognition validates our commitment to helping customers achieve complete cyber resilience.
Fantastic Rootkits: And Where To Find Them (Part 3) - ARM Edition
In this blog, we will discuss innovative rootkit techniques on a non-traditional architecture, Windows 11 on ARM64. In the prior posts, we covered rootkit techniques applied to a modern Windows 10 OS (Part 1) and rootkit analysis of current threats for Intel x86-64 (Part 2). Although we have yet to come across any malware family in the wild targeting this platform, we may see it in the near future as Windows on ARM devices grow in popularity.
WormGPT and FraudGPT - The Rise of Malicious LLMs
As technology continues to evolve, there is a growing concern about the potential for large language models (LLMs), like ChatGPT, to be used for criminal purposes. In this blog we will discuss two such LLM engines that were made available recently on underground forums, WormGPT and FraudGPT. If criminals were to possess their own ChatGPT-like tool, the implications for cybersecurity, social engineering, and overall digital safety could be significant.
Rubrik and Laminar: Together Securing the World's Data
Today we are excited to share that Rubrik has entered into an agreement to acquire Laminar, the leader in Data Security Posture Management (DSPM), to realize a common vision to secure the world’s data. The combination will create the industry’s first offering to combine cyber recovery and cyber posture and deliver complete cyber resilience across enterprise, cloud, and SaaS.
Targeting the Ransomware Kill Chain | Cyber Week Tel Aviv
Ransomware attacks cost manufacturing sector $46 billion in downtime since 2018, report claims
Newly-released research reveals the eye-watering costs that the manufacturing sector has suffered in recent years at the hands of ransomware. The analysis, by Comparitech, looked at 478 confirmed ransomware attacks on manufacturing companies between 2018 and July 2023, in an attempt to determine their true cost.
New Rilide Stealer Version Targets Banking Data and Works Around Google Chrome Manifest V3
Trustwave SpiderLabs discovered a new version of the Rilide Stealer extension targeting Chromium-based browsers such as Google Chrome, Microsoft Edge, Brave, and Opera. This malware uses a creative way to work around the Chrome Extension Manifest V3 from Google which is aimed at blocking the installation of malicious extensions for chromium browsers.
Bad Actor Uses Fake Android Chat to Install Malware
Researchers at CYFIRMA warn that the Bahamut threat actor is using a malicious Android app to deliver malware. “The suspected Android malware, known initially as ‘CoverIm’ was delivered to victims via WhatsApp, and was found to be disguised as a dummy chatting application named ‘SafeChat,’” the researchers write.
The Urgent Need For Cyber Resilience in Healthcare
A US hospital closed two years after a ransomware incident, highlighting that the health sector continues to be under threat.
Honeypot Recon: New Variant of SkidMap Targeting Redis
Since Redis is becoming increasingly popular around the world, we decided to investigate attacks on the Redis instance. We didn’t have to wait long for the first results of the Honeypot. The trap caught an activity about which the Western world does not hear too often while analyzing SkidMap. More importantly, this variant turned out to be a new, improved, dangerous variation of the malware. Its level of sophistication surprised us quite a bit.
CTI Roundup: Realst Malware targets MacOS, Infostealer Malware Sees Exponential Growth
Realst malware targets macOS Sonoma ahead of public release, infostealer malware sees exponential growth, and new Nitrogen malware spreads via Google Ads for ransomware attacks.
What Is Cybercrime: The Different Types You Need to Look Out For
WannaCry Ransomware Attack: What, Who, Why, When, & How to Stay Protected?
The May 12, 2017, WannaCry ransomware attack was one of the most devastating and globally widespread computer infections. The next WannaCry is prepared and about to occur in 2023, claims Kaspersky. The potential reason is that the biggest and most devastating cyber epidemics happen every six to seven years. Here are some helpful tips to stay protected against WannaCry ransomware.
Detecting Storm-0558 using Corelight evidence
While there have been many intrusions, compromises, breaches, and incidents that have made news in the IT and InfoSec industries throughout 2022 and into this year, when events or threats like Storm-0558 gain coverage by mainstream media, we often get questions about Corelight’s ability to detect threats through our sensors, products & platform.