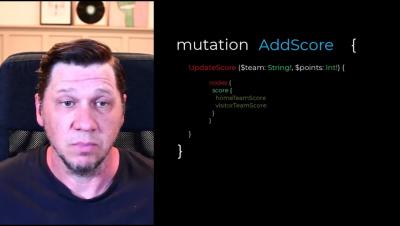
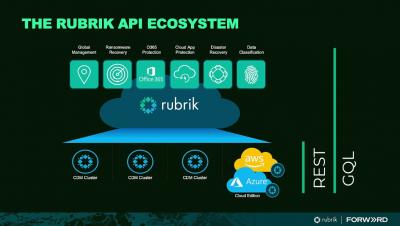
Detecting Ransomware on Unmanaged Devices
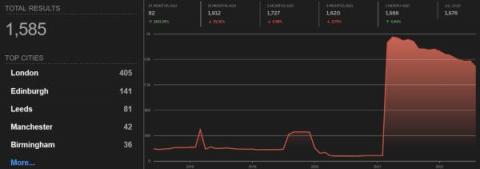
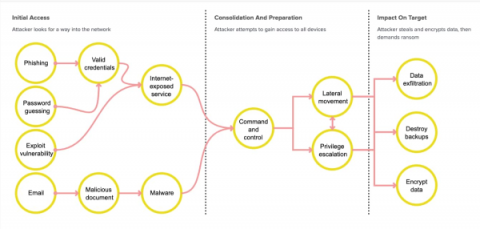
“If a tree falls in a forest and no one is around to hear it, does it make a sound?” If an unmanaged device is infected with ransomware, will the security operations team receive an alert? Consider a contractor or employee who uses their personal laptop for work. If that device becomes infected with ransomware, not only does it pose a risk to the organization’s data and a risk to other devices within the organization, but the device is not centrally managed.