Black Kingdom Ransomware
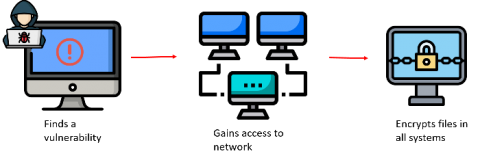
Hot on the heels of 'Dearcry'[1], yet another ransomware threat has been observed as targeting Microsoft Exchange servers vulnerable to recently reported critical vulnerabilities[2]. Dubbed 'Black KingDom', this ransomware threat has reportedly been deployed through a web-shell that is installed on vulnerable Microsoft Exchange servers following the exploitation of the vulnerability chain that results in both remote code execution (RCE) and elevated privileges.