Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2022
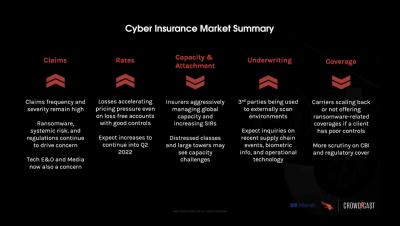
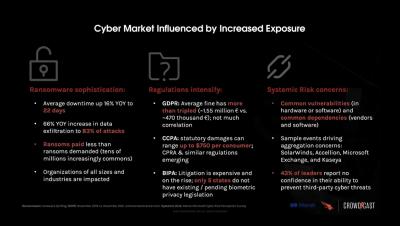
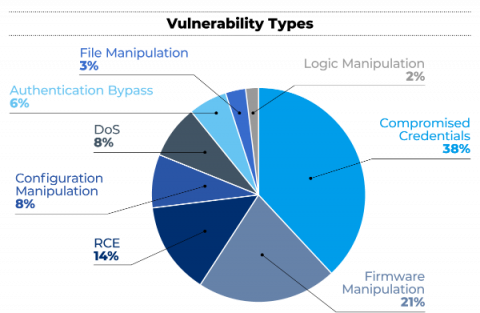
Identity is Key to Bolstering CI Controls
Tales from the Dark Web: How Tracking eCrime's Underground Economy Improves Defenses
Cybercriminals are constantly evolving their operations, the methods they use to breach an organization’s defenses and their tactics for monetizing their efforts. In the CrowdStrike 2022 Global Threat Report, we examined how the frequency and sophistication of ransomware attacks has grown in the past year.
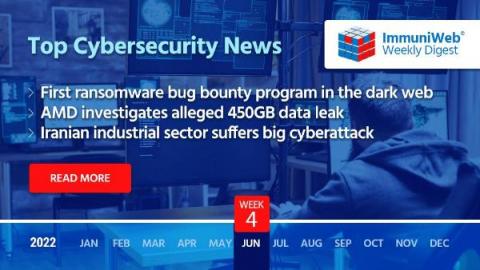
LockBit Ransomware Gang Introduces the First Ransomware Bug Bounty Program in the Dark Web
Read also: RansomHouse extortion gang allegedly stole 450GB of data from AMD, one of Iran’s major steel companies was hit by a cyberattack, and more.
The Emotet Botnet is Back and Stronger Than Ever
Emotet, one of the most pervasive and destructive botnets in use today, first appeared in 2014. Despite its age, Emotet is still going strong and shows no signs of disappearing anytime soon.
CrowdStrike Falcon Pro for Mac Achieves 100% Mac Malware Protection, Wins Fifth AV-Comparatives Approved Mac Security Product Award
CrowdStrike believes that continuous testing and evaluation by third-party organizations is critical in helping customers make informed decisions about which security solution best fits their needs. This is why CrowdStrike continues to participate in more third-party testing than any other next-gen endpoint cybersecurity vendor.
What is Double Extortion Ransomware? And How to Avoid It
As the internet grows, so does the sophistication and capabilities of cyber attacks. Cybercriminals constantly develop new ways to exploit even the most complex networks and servers. One of the newer types of attacks caused major headlines in 2020 and continues to be a force to be reckoned with for even the largest companies and organizations. It's called a double extortion ransomware attack. Becoming a victim of these vicious attacks can lead to devastating consequences.
Emotet: Still Abusing Microsoft Office Macros
In April 2022, Netskope Threat Labs analyzed an Emotet campaign that was using LNK files instead of Microsoft Office documents, likely as a response to the protections launched by Microsoft in 2022 to mitigate attacks via Excel 4.0 (XLM) and VBA macros.
Are Protection Payments the Future of Ransomware? How Businesses Can Protect Themselves
Ransomware has matured significantly over the previous decade or so. Initially thought to be a relatively basic virus that could be contained on a floppy disk, it can now damage global business infrastructures, stop healthcare systems dead in their tracks, mess with fuel supply networks, and disrupt transportation infrastructure. Its simplicity is what makes it so appealing to criminals. The attacks don’t have to be very sophisticated to cause significant harm and extort ransom payments.
How Healthcare Organizations can Secure Massive Unstructured File Data using Rubrik
The digitization of healthcare has caused an unrelenting growth trend in unstructured data, with no slowdown in sight. Patient records, lab tests, PACS imaging, and research data are now stored electronically and as the amount of healthcare data continues to skyrocket, so do data vulnerability and security risks.
The Call Is Coming from Inside the House: CrowdStrike Identifies Novel Exploit in VOIP Appliance
CrowdStrike Services recently investigated a suspected ransomware intrusion attempt. The intrusion was quickly stopped through the customer’s efforts and those of the CrowdStrike Falcon Complete™ managed detection and response (MDR) team, which was supporting this customer’s environment.
Threat Update: Industroyer2
The Splunk Threat Research Team (STRT) continues to monitor new relevant payloads to the ongoing conflict in Eastern Europe. One of these new payloads was found by the Ukranian CERT named “Industroyer2.” The name of this new payload references the original "Industroyer" malicious payload used against the country of Ukraine's power grid in 2016 and allegedly was able to affect a fifth of the power capacity of the city of Kyiv.
Ransomware attack vectors: what your organisation needs to look out for
OT:ICEFALL: 56 Vulnerabilities Caused by Insecure-by-Design Practices in OT
It has been 10 years since Project Basecamp, a research project conducted by Digital Bond that investigated how critical operational technology (OT) devices and protocols were, to use the term they coined, “insecure by design.” Since then, we have seen hugely impactful real-world OT malware such as Industroyer, TRITON, Industroyer2 and INCONTROLLER abusing insecure-by-design functionality.
BlackGuard Stealer Targets the Gaming Community
How to stop sophisticated ransomware attacks
The number and frequency of ransomware cyberattacks are growing every year. The European Union Agency for Cybersecurity (ENISA) recorded a 150% increase in 2020 alone and, as of last year, ransomware attacks have become the number one threat. Added to this, the recovery costs and downtime incurred can be up to 10 to 15 times higher than the ransom demanded by cybercriminals.
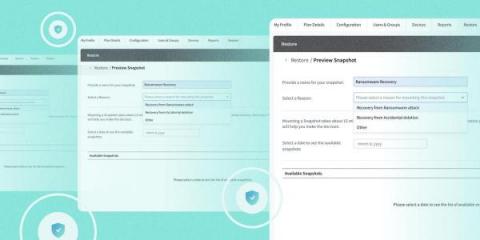
How Egnyte Built Snapshot Recovery to Mitigate Ransomware Attacks
As companies accumulate and store large amounts of business data in the cloud, data security and governance become a major concern. More than 16,000 companies use Egnyte to manage, secure, and govern their content. These businesses rely on the unified platform to keep their business running smoothly, because data loss due to ransomware attacks or accidental file deletion could have profound impacts on their bottom lines.
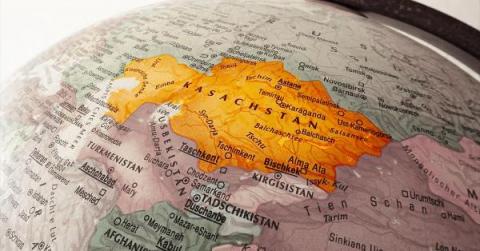
Lookout Uncovers Hermit Spyware Deployed in Kazakhstan
Lookout Threat Lab researchers have uncovered enterprise-grade Android surveillanceware used by the government of Kazakhstan within its borders. While we’ve been following this threat for a while using Lookout Endpoint Detection and Response (EDR) these latest samples were detected in April 2022, four months after nation-wide protests against government policies were violently suppressed.
Royal Flying Doctor Service Queensland Protects The Crown Jewels of Patient & Aviation Data
How Rubrik Supports the NIST Cybersecurity Framework Profile for Ransomware Risk Management
Rubrik was built on a foundation of Zero Trust architecture. The National Institute of Standards and Technology (NIST) is a United States federal agency that works with organizations of all sizes to help them implement cybersecurity best practices.
A System Integrator's Guide to Delivering Zero Trust Data Security with Rubrik
The volume and frequency of ransomware attacks have increased significantly this past year. In fact, the number of ransomware attacks has nearly doubled in 2021 as compared to 2020. The impact of a breach is multi-fold and stretches well beyond the commonly acknowledged risks of downtime cost, impact on the brand, and the actual ransom paid. This has prompted a paradigm shift in how organizations and system integrators look at their cybersecurity strategy.
Industroyer2 and INCONTROLLER: New Findings and How Forescout Protects Against the Most Recent ICS-Specific Malware
In our new threat briefing report, Forescout’s Vedere Labs presents the most detailed public technical analysis of Industroyer2 and INCONTROLLER (also known as PIPEDREAM), the newest examples of ICS-specific malware that were disclosed to the public almost simultaneously, on April 12 and 13. Thankfully, both Industroyer2 and INCONTROLLER were caught before causing physical disruption.
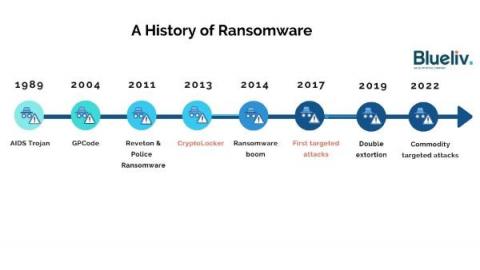
A History of Ransomware
Ransomware is the biggest cyber threat to businesses. First burst onto the scene in 1989, it has evolved significantly over the past few years from widespread attacks to highly targeted ransomware-as-a-service (RaaS) operations affecting organizations of all sizes and sectors. This article takes a look at the evolution of the ransomware ecosystem – what it looks like today, and how it has changed over time.
The State of Security: Ransomware
Sophos Labs recently released its annual global study, State of Ransomware 2022, which covers real-world ransomware experiences in 2021, their financial and operational impact on organizations, as well as the role of cyber insurance in cyber defense. The report, which surveyed 5,600 IT professionals in mid-sized organizations across 31 countries, shows that ransomware attacks are increasing and becoming more sophisticated.
NJ TRANSIT Protects the Garden State passengers' economic and social well-being from cyber threats
Automating the Security Protections rapid response to malware
Make Account Compromise a Non-Issue: Introducing Immutability for Microsoft Azure VMs
Author Brian Mislavsky Rubrik Storage Tiering for Microsoft Azure now leverages Azure Blob immutability by default. In our Winter Release, we introduced Storage Tiering for Microsoft Azure as a way for Rubrik customers to further protect workloads in Microsoft Azure by enabling the ability to logically air gap data between Azure Subscriptions as well as potentially decrease long term storage costs by almost 40%.
Conti ransomware incapacitates Costa Rica's government: The FBI, CISA, the NSA, and Secret Service recommend mitigation strategies
Weeks after President Rodrigo Chaves Robles became Costa Rica’s 49th president, he had to tackle the country’s largest cyberattack ever. Costa Rica declared a state of emergency following a series of detrimental ransomware attacks carried out by the Conti ransomware gang.
Possible Link Between Jester Stealer and Eternity Stealer
Jester stealer is an information stealer that has been around since mid-July 2021. Originally sold by the Russian speaking threat group "Jester_Stealer", in several underground forums and Telegram channels, they operate under a Malware-as-a-Service (MaaS) model and present themselves as a group of programmers. Here we delved into the Jester stealer functionalities with a code-level analysis and highlight the possible link between Jester stealer and the new breed of Eternity stealer.
Worried about ransomware? Start with a plan
You don’t need me to tell you what a ransomware attack could do to your business. We’ve all read the stories. Even the largest multinationals have been crippled by malware encrypting or stealing sensitive data. The result is a Hobson’s choice for IT managers: pay the criminal gang an exorbitant ransom demand or face costly downtime, reputational damage, and regulatory scrutiny. Thankfully, your fate is in your hands. Ransomware attacks aren’t random.
How Lookout Prevents Ransomware Attacks | Lookout
Bumblebee Loader Linked to Conti and Used In Quantum Locker Attacks
Kroll has recently observed a new malware strain called “Bumblebee” operating as a loader, delivered via phishing email, in order to deploy additional payloads for use in ransomware operations. The malware takes its name from the unique user-agent (since changed), which it used to connect to command and control (C2) servers. It was first reported by Google's Threat Analysis Group (TAG) in March 2022, with the first sample submitted to VirusTotal on March 1.
Take a Look Into the Rubrik Platform
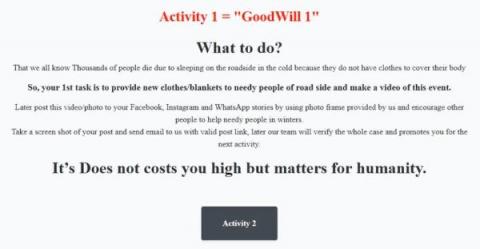
GoodWill Ransomware? Or Just Another Jasmin Variant?
In March 2022, researchers spotted a new ransomware family named GoodWill, with a new method to collect the ransom. Instead of requesting payment through crypto coins like other threats such as Night Sky or Hive, GoodWill requests that its victims help vulnerable people by following a sequence of steps, such as donating clothes, feeding less fortunate children, or providing financial assistance to hospital patients.
Can Macs Get Ransomware? Examples + Prevention Strategies
Many of the most prolific ransomware attacks to hit the news, such as Wannacry and Petya in 2017, affected PC users only. The distinct absence of Apple computers in the long list of victims has many Mac users wondering if ransomware attacks are a cyber threat they need to worry about. Can ransomware affect Macs? Short answer: Yes. While rare, security researchers have noted examples of Mac-compatible ransomware variants.
Avoid Taking Shortcuts - New Emotet Technique
Tiny Banker Trojan
While living in the 21st century, no one can live off offline modes of payment all the time. Financial institutions, especially banks, have gone the extra mile to ease the process for their clients in the meantime, attracting cybercriminals and their ever-changing malware as threats to their information security. Tinba is one such threat especially plaguing Windows. Read on to know more about the tiny virus and its not so tiny implications.
Three Ransomware Myths
Coffee Talk with SURGe: 2022-MAY-31 Follina MSDT zero day, ransomware roundup, supply chain risk
5 ways to prevent Ransomware attacks
“Ransomware has become the enemy of the day; the threat that was first feared on Pennsylvania Avenue and subsequently detested on Wall Street is now the topic of conversation on Main Street.” Frank Dickson, Program Vice President, Cybersecurity Products at IDC.