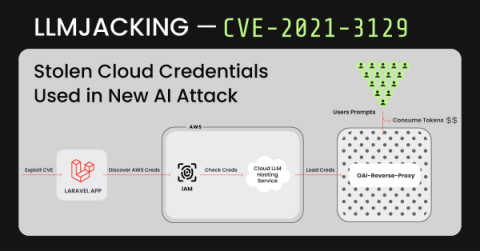
Asset hijacking: the digital supply chain threat hiding in plain sight
The digital supply chain refers to the chain of third-party digital tools, services and infrastructure that is depended on for a particular first-party service (such as your website or SaaS platform). In an ever-changing digital landscape, supply chains can be brittle with many unseen risks. The nature of supply chain risk is transitive; any part of the often long and complicated digital supply chain can be compromised, causing all components downstream of it to also be compromised.