Top 5 Zero Trust Vendors in Cybersecurity in United States You Should Know
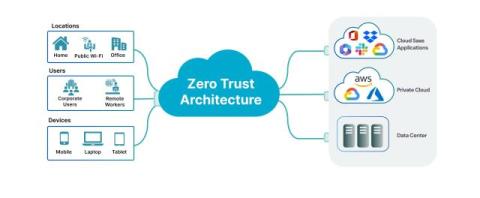
Because cyber dangers are always changing, businesses are moving toward safer and more proactive ways to keep their data and networks safe. Zero Trust Security is one of these frameworks that is becoming more popular. It is based on the idea of "never trust, always verify." Zero Trust constantly checks and authorizes every user and device before letting them access sensitive data or systems. This is done instead of thinking that internal users or devices are reliable.