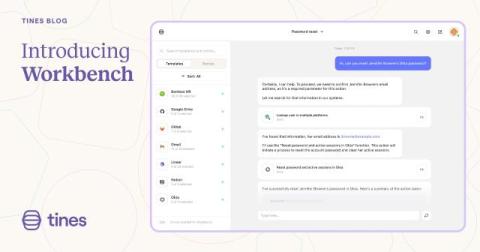
Introducing Tines Workbench
You trust us with your most important workflows, and we take that trust seriously. In developing AI in Tines, we’ve been laser-focused on helping users leverage AI without exposing their organizations to security and privacy risks. But we also spoke with so many teams struggling to fully realize AI's potential impact. They wanted AI to do more, while still preserving those all-important security and privacy guardrails.