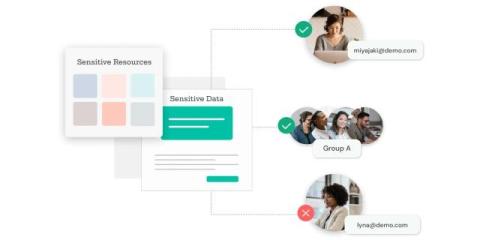
Sequoia spotlight: Deploying the newest macOS with Endpoint Central
Apple released its new macOS Sequoia 15.0 on Sept. 16, and we at ManageEngine are excited to announce our support from the day of its release. Before we get into the details, let’s look at which devices are eligible for the facelift. Source: Apple Sequoia was unveiled at WWDC 2024 with a range of features around privacy, security, and its much-awaited Apple Intelligence.