Supply chain integrity, transparency and trust is now firmly on the agenda
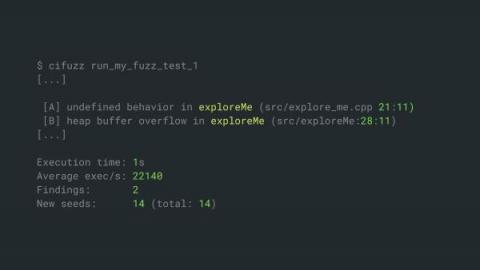
Supply chain risk continues to make headlines, from Solarwinds and Kaseya to last week’s announcement of a patch for the OpenSSL vulnerability, and the latest cybersecurity review from the U.K.’s National Cyber Security Centre highlights the serious threats posed by supply chain attacks.