|
By Robin Bryce
To set up the “surprise”, let’s start with a trick question: How many roots do I need in my life?
|
By Steve Lasker
In a time when everything said, whether factual, fake, or AI-created, may be recorded and posted on the internet, it’s more important than ever to ensure that what was recorded accurately represents a point in time. When someone claims you said, “I was Smoking on a flight, watching Star Wars, the best special effects movie of all time,” was that a false claim? Did they include the date and the context?
|
By Jon Geater
And we never were. From the very beginning, DataTrails has been committed to bringing the power of transparency and trust technologies to regular enterprises, making very new and complex technology accessible to those who need it most: the existing industries and companies who run our world.
|
By Steve Lasker
In a world where software is produced, distributed, and re-distributed, how do you ensure the software you consume is authentic and safe for your environment? How do you know the software you deployed yesterday is safe today? Most software exploits are discovered after the software has been deployed, which raises the question: It’s not just about getting software updates, as the majority of exploits are distributed as updates. Staying updated isn’t the most secure.
|
By DataTrails Team
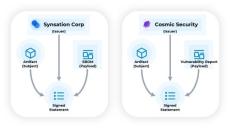
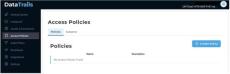
Signing up with DataTrails comes with the ability to share your audit trails with your business partners, other applications, and your internal team. Access policies control users, apps & organizations’ read & write privileges to provenance data in DataTrails. If you’re using an integration, access policies offer a way to fine-tune these integrations, giving specific permissions to add to and read your records.
|
By Will Cumpston
Data provenance is a technology field that aims to help businesses increase trust through transparency of data, specifically by tracking the origin, change, and history of data and making it verifiable. Recently, the benefits of data provenance have become more important than ever. With the emergence of generative AI, all it takes are a few button clicks for anyone to create or manipulate data and convince others that fake data is trustworthy and real.
|
By Will Cumpston
The average cost of invoice fraud to middle-market businesses is almost $280,000 per year. Invoice fraud affects businesses of all sizes, and the levels of fraud have increased in part because it’s not possible to authenticate all invoices that come in manually, with many businesses paying out invoices without authentication if they’re under a certain amount. Today’s information security rules and regulations can’t keep up.
|
By Rusty Cumpston
To share an immutable audit trail, you can do this with a link or a QR code that is automatically created when provenance and authenticity metadata is recorded in your DataTrails account. After you sign in to your DataTrails account on your smartphone, Anyone can use Instaproof or the DataTrails API to verify the authenticity, provenance and audit trails of public images.
|
By Colin McCabe
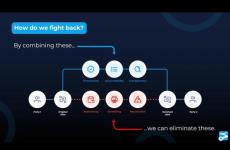
In the age of Gen AI, it is now apparent that we can no longer trust what we see and read. The fakers have the upper hand: while typical security approaches rely on scaling up teams, attacks scale at the press of a button. To safely move forward and realize the benefits Gen AI enables, we need a better trust model that adds integrity, transparency and trust to all data and a common provenance format that captures origin, authenticity and lineage information. We must verify data before we use it.
|
By Colin McCabe
As supply chains continue to evolve and new Al technology becomes part of every business, traditional trust systems that rely on human interactions to verify and validate data will struggle to keep pace. Digital supply chain practices from media through software to physical goods must adapt to this changing global technology landscape. The innovations unleashed in GenAI have made it apparent that we can no longer trust what we see and read; we must verify data before we use it.
|
By DataTrails
This demo is an example of how DataTrails is used to collect information from different databases and different suppliers to form a single source of truth for the full life cycle of an asset. The video shows how multiple parties can track disposable containers for nuclear waste on the DataTrails transparent platform.
|
By DataTrails
DataTrails revolutionizes data integrity and transparency by enabling control over data flows, validating data sources, and constructing mutually accountable records. This approach not only meets the immediate need for secure and trusted data exchange but also lays the groundwork for AI systems to automate sensitive workflows confidently. DataTrails' patented distributed ledger technology underpins AI-driven decision-making, ensuring resilience, explainability, and regulatory compliance.
|
By DataTrails
When you connect DataTrails to your Dropbox account we automatically create a small amount of additional metadata about your files each time they change, and record that information on an immutable ledger. Those files are now equipped with long-term integrity and the ability for anyone to instantly verify the provenance and authenticity of your digital content using our free no-need-to-sign-up tool, Instaproof. And best of all, you don’t need to change your workflows! You can continue to email your files around, or send them through your favorite transfer app, and wherever they end up their provenance will be verifiable.
|
By DataTrails
Unravel the truth behind every image with Digimarc and DataTrails. Our demo showcases our approach to exposing fakes and validating authentic images. Verifying the origin of an image is as easy as drag and drop. Witness the innovative combination of Digimarc's watermarking technology and DataTrails' immutable audit trails, which together offer a robust solution to the challenges of digital misinformation. This powerful collaboration ensures the integrity of images online, making it simpler than ever to distinguish genuine content from deceptive visuals.
|
By DataTrails
Trust in digital media is consequential — from the practical verification of the source of a news photograph to the less visible web infrastructure that impacts society and economies of scale. In this Community Showcase, we’re focusing on solutions that build transparency into our digital ecosystem. See Jon Geater's demo on maintaining the integrity of data across business and application boundaries with the DataTrails platform.
|
By DataTrails
We've listened, we've learned, and the market has definitely spoken! Our old name just wasn't working: it was hard to pronounce, hard to spell, and hard to understand what we do. Even if the ‘archivist' leap was made it didn't carry our special mission with it. At the same time, our customers are increasingly telling us that what we do best is help them build immutable audit trails for all their business data: documents, files, images and other types of digital content.
|
By DataTrails
Bring provenance to your Dropbox files with RKVST. How can you prove that your work is original, authentic, and trustworthy? How can you protect it from being copied, manipulated, or misused? That’s where RKVST comes in, documenting the origin, history, and validity of your content, such as text, images, audio, or video, so you can prove where it came from. With RKVST you can: And with RKVST for Dropbox creating and recording the provenance metadata is as easy as a click of a button. Watch our video to find out how.
|
By DataTrails
Bring provenance to your Dropbox files with RKVST. How can you prove that your work is original, authentic, and trustworthy? How can you protect it from being copied, manipulated, or misused? That’s where RKVST comes in, documenting the origin, history, and validity of your content, such as text, images, audio, or video, so you can prove where it came from. With RKVST you can: And with RKVST for Dropbox creating and recording the provenance metadata is as easy as a click of a button. Watch our video to find out how.
|
By DataTrails
Delve deep into Cyber Resilience with RKVST in just under a minute! This short clip demystifies Cyber Security, emphasizing the real needs of businesses - resilience and security that supports operational objectives. 🌐 Quick Insights: Understanding Cyber Security beyond 'buying one security' Unpacking the essence of business resilience with RKVST.
|
By DataTrails
Spot fake content and data with RKVST's Instaproof.
- January 2025 (1)
- September 2024 (1)
- May 2024 (1)
- February 2024 (4)
- January 2024 (3)
- December 2023 (3)
- November 2023 (6)
- October 2023 (5)
- September 2023 (1)
- August 2023 (3)
- July 2023 (1)
- June 2023 (1)
- May 2023 (4)
- April 2023 (2)
- March 2023 (2)
- February 2023 (1)
- January 2023 (2)
- December 2022 (1)
- November 2022 (4)
- October 2022 (3)
- August 2022 (1)
- July 2022 (3)
- June 2022 (2)
- May 2022 (1)
- March 2022 (2)
- February 2022 (2)
- January 2022 (4)
- December 2021 (2)
- November 2021 (1)
- October 2021 (2)
- September 2021 (2)
DataTrails is a service for developers to continuously prove who did what when which brings confidence in critical business decisions.
DataTrails’s Zero Trust Fabric approach empowers enterprises with the benefits of DLT and trustworthy supply chain visibility through a simple agentless API that integrates easily with existing software, systems, and security policies, enabling you to continuously verify then trust data that originates outside your domain of control before making critical decisions.
Key Features:
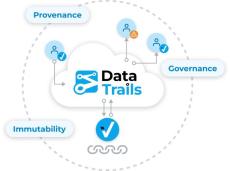
- Provenance: Proof of origin and life history. Continuously capture the full lineage and pedigree of assets. Help your users identify the who, what, and when of ownership, maintenance, audits, and change approval for critical assets.
- Governance: Producers can precisely control information flows to the right users at the right time – inside and outside your organization. Put your business users in control of sharing policies.
- Immutability: An unbreakable chain of evidence is preserved for all stakeholders. Continuous assurance and reliable access to data enables faster, more confident critical decisions.
If you rely on shared data with your supply chain partners you need a zero trust fabric.