Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Cyber Insurance: Is It Fit For Purpose? | Razorwire Podcast
Do AI and Malicious Actors Have Access To Data Now | Cyber Security
How to Modernize Access Control for Cloud Applications with Or Weis
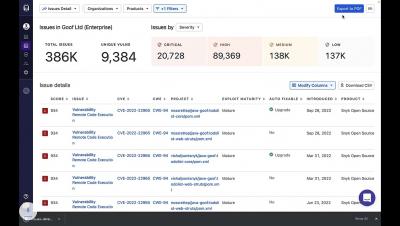
Introduction to Snyk's revamped reporting
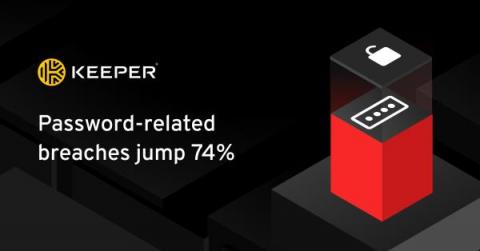
New Microsoft Research Emphasizes Critical Importance of Password Management
It’s no surprise that cyberattacks are skyrocketing. Report after report indicates they’ve exploded in recent years as cybercriminals take advantage of the rapid proliferation of endpoints, growing reliance on digital devices, and shift toward remote and hybrid work. However, as the number of attacks increases, the types of attacks remain surprisingly simple. You guessed it. They’re still going after passwords, credentials and secrets.
How to Keep Kids Safe Online
We live in the 21st century, where now kids are able to access the internet on their own from as early as 8 years old. Today’s youth are often called “digital natives” because they are so comfortable with living online. But as much as we may admire their proficiency with their devices, we shouldn’t forget that security is probably not top of mind.
CVE-2022-27510: Citrix Gateway and Citrix ADC Critical Authentication Bypass Vulnerability, along with CVE-2022-27513 & CVE-2022-27516
Six Actively Exploited Vulnerabilities Patched in Microsoft's November Security Update
WEF Report Details Best Practices for Zero Trust Deployment
Cybersecurity, like broader technological disciplines, is an ever-changing landscape that industry professionals must adapt to. The zero-trust model of cybersecurity has grown recently as organizations update their security practices to keep pace with, and stay ahead of evolving threats. Zero Trust Network Access (ZTNA) increased by 230% from 2019 to 2020, and more than 80% of C-suite leaders cite zero-trust as a priority for their enterprises.