Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
JFrog Xray Integration with AWS Security Hub
SecOps demands vigilance, but it requires visibility, too. With JFrog’s latest integration for Xray with AWS Security Hub, you can help make sure that discovered vulnerabilities are not just seen, but quickly acted on. AWS Security Hub is the cloud security posture management service available to AWS users. It provides central security administration across AWS accounts, performing security best practice checks, aggregating alerts, and enabling automated remediation.
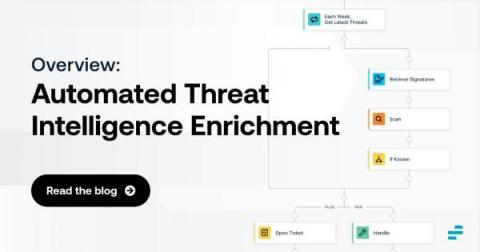
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.
CCPA Compliance Vs CPRA Compliance
The California Consumer Privacy Act (CCPA) is a law that was signed on June 28, 2018, that established and promoted the consumer privacy rights and business obligations concerning the collection and sales of personal information of citizens of California. The CCPA came into effect on January 1st, 2020. Soon after in November 2020, Proposition 24, known as the California Privacy Rights Act of 2020 (CPRA) was introduced which is soon to replace the CCPA Compliance.
Keeper vs Delinea: Which Privileged Access Manager is Better for Your Business?
Privileged access management (PAM) uses cybersecurity strategies, tools, and technologies to control access permissions for users and systems across an IT environment. The goal is to hone in on privileged access controls to mitigate the risks of a cyberattack. According to the 2021 Privileged Access Management Solutions Market Offering, the global PAM solutions market size was valued at $2.47 billion in 2020 and is projected to reach $19.73 billion by 2030.
Address the Cybersecurity Skills Shortage by Building Your Security Stack with the CrowdStrike Store
The increase in attack sophistication coupled with the decline of skilled security staff continues to put pressure on organizations and their teams by minimizing their ability to effectively see and control risks within the enterprise. This is only made more difficult as teams find themselves patching together disparate solutions, resulting in labyrinthian security stacks and a heavily siloed environment.
CrowdStrike and AWS Expand Partnership to Offer Customers DevOps-Ready Security
Cloud-based services are augmenting business operations and being adopted at a record pace. In fact, Gartner® estimates “more than 85% of organizations will embrace a cloud-first principle by 2025 and will not be able to fully execute on their digital strategies without the use of cloud-native architectures and technologies.”
SecurityScorecard and AWS Help Make Secure Software Procurement Faster and Easier
Organizations increasingly rely on third parties for business operations, and as a result are working with more digital suppliers than ever. According to Gartner, 60% of organizations work with more than 1,000 third parties and this number will grow. High-profile vulnerabilities such as Log4Shell are a constant reminder of the risks posed by a breakdown in the software supply chain. This has spurred enterprises to increase the rigor of software risk assessments to ensure supply chain security.
Tines joins the AWS Partner Network
Tines is delighted to announce we have joined the AWS Partner Network as a Select Partner, and our no-code automation platform is now live on AWS Marketplace. Additionally, we are very proud to have recently won an AWS Software Startup Award. The awards were created to shine a spotlight on innovative B2B/SaaS startups in the UK and Ireland.
The lifecycle of a software vulnerability
This is the second part of a three-blog series on startup security. Please check out part one too. The anatomy of a software vulnerability is a bit like mercury accumulation in seafood. Trace amounts of naturally occurring mercury in seawater is absorbed by algae and bioaccumulates up the food chain. Large fish at the top of the food chain contain the most mercury and should be consumed in limited quantities.