Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Best practices for your first 30 days with Snyk
This post is applicable to Business plan and Enterprise plan customers. Adopting a new platform can seem intimidating, but with Snyk it doesn’t have to be. We have three tips to help you roll out Snyk, and have a seamless and successful first 30 days across your business or enterprise. Before you start inviting team members and importing projects, you’ll want to consider your account strategy, set up single sign-on (SSO), and configure your first organization.
Which TLS version is obsolete?
Want To Become A Red teamer? This Is What You Need To Know
Everyone loves buzz words, no? Red team is the newest (well... not that new) coolest thing on the streets of information security city and many cybersecurity pros want to jump right in and become involved in Red team activities at their company. However, there is more to being a Red team member than just signing up.
CVE-2022-22280 - Critical SonicWall Vulnerability Impacting Analytics On-Prem and Global Management System Products
Tackle cloud-native adoption and security hurdles with Coforge and Sysdig
The desire to take advantage of the modern cloud-native paradigm has forced many enterprises to rush to production with Kubernetes and containerized applications. Often, the incorrect expectation with cloud-native adoption is that Ops teams would be able to easily transition their existing security and operational practices, workflows and tooling to these new software development platforms and everything would still work as before.
How DevOps and CIS Security Controls Fit Together
The Center for Internet Security’s Critical Security Controls has become an industry standard set of controls for securing the enterprise. Now on version 8, the original 20 controls are down to 18 with several sub controls added. The first six basic controls can prevent 85 percent of the most common cyber attacks, and even though the controls have been developed with traditional data centers and process in mind, there is no reason they can’t be adapted to DevOps practices.
The State of Data Security in 2022: The CISOs Perspective
In the two years proceeding from the beginning of the COVID-19 pandemic, the business world has been transformed on a grand scale. Organizations have created more data than ever before, data is now spread across a wider attack surface, putting it at a heightened risk of becoming a compromised risk. The manner and location of data storage and correspondence has had to shift to meet the needs of remote and hybrid workers, with companies being forced to take a more rigorous approach to data security.
How should the security industry innovate against email risks over the next five years?
Our research has revealed that 80% of security professionals have experienced increased security threats since shifting to remote work. To stay protected against attacks and reduce the chances of losing significant amounts of money, putting their users at risk, or destroying their reputation, organizations must do more to innovate against email risks. In our most recent report, Cybersecurity experts' views on email risk within Microsoft 365, we identify many of the risks Microsoft 365 users face.
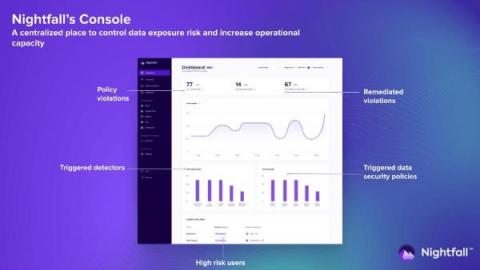
Nightfall's New Console Provides Actionable Analytics & Centralized UI for Solving Data Security Risk
The Nightfall platform is a SaaS data protection platform already known for its high accuracy findings and analytics. Now, thanks to new features baked into the Nightfall Console, users will have enhanced analytics functionality through an elegant and easy to navigate dashboard interface. Watch the video demo below for a walkthrough of changes, or read the rest of the post to learn more.