Announcing the Nightfall Developer Platform - APIs for Building Data Protection into Any Application
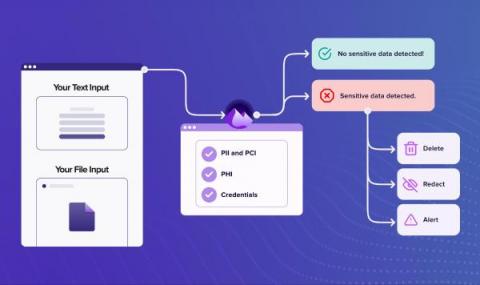
Nightfall’s vision is to power data protection in every app or service. Our native SaaS integrations for apps like Slack, GitHub, and Google Drive already protect organizations, ranging from small startups to the Fortune 100, against data leaks with our machine learning-powered detection engine. Today, we’re excited to announce the launch of the Nightfall Developer Platform, so you can build data discovery, classification, and protection using our powerful APIs.