How To Integrate Endpoint DLP Into Your Company's Security Policy
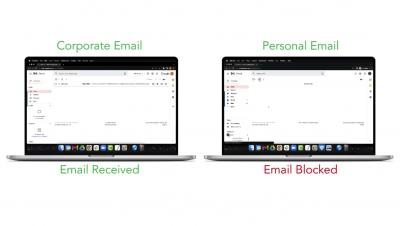
Even before the pandemic, many companies had a relaxed approach to the devices employees brought to work. In fact, many businesses had BYOD (bring your own device) policies that allowed team members to work on personal laptops or cell phones. By one account, 75% of employees use their personal cell phones for work. The rise of remote work has only escalated the use of tablets, laptops, and mobile phones for professional use.