Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cyberattacks
Cyber Attacks Are Coming, Cyber Security Must Ensure Business Survivability
NPM security: preventing supply chain attacks
NPM security has been a trending topic in the media in recent years, mostly in reference to npm packages available on the ecosystem rather than the npm registry itself. The increasing security risk, that applies to developers and software we build, makes it even more important to understand how to prevent supply chain attacks and other security vulnerabilities related to software development life cycle.
The Power of Manual Penetration Testing in Securing Your Attack Surface
When it comes to protecting software, don’t count on automated testing to find all the vulnerabilities in your code. Here’s why manual penetration testing is more essential (and more accessible) than one might think.
Remember, Remember: What Guy Fawkes and the Gunpowder Plot Can Teach Us About Modern Cyber Attacks
10 years ago I moved to the UK and made it my home, and I love living here. I like Marmite, debates over whether the evening meal is dinner, tea, or supper, the constant requirement to remark upon the weather… and the many bizarre traditions. One of these bizarre traditions is Bonfire Night, celebrated on 5th November each year to commemorate the Gunpowder Plot when a bunch of conspirators (including a man called Guy Fawkes) tried to blow up Parliament and King James.
Demystifying Breach Notification
As the number of high-profile cyberattacks and data breaches has increased in recent years, more companies have made investments to better secure their systems and develop incident response plans. While these are essential concerns, a firm’s obligations don’t simply end when a threat is removed from the network and they are able to resume normal operations. They must also notify those whose data may have been impacted by the breach.
KillNet Operations Against U.S. Targets Persist With Attempted Airport Website Attacks
In October, BleepingComputer reported that the websites of several airports were experiencing service disruptions after the KillNet threat actor group announced that they would target airports throughout the U.S.
The Top Cyber Attacks of October 2022
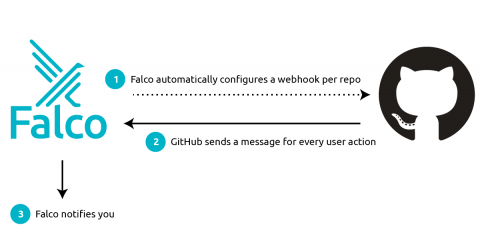
Responding to the Dropbox Breach with a Falco GitHub Plugin
On November 1st, Dropbox disclosed a security breach where the attackers stole over 130 code repositories after gaining access to one of the employee’s GitHub accounts using the stolen credentials of that employee via a well-designed phishing attack.