The Only DORA Compliance Checklist You Need
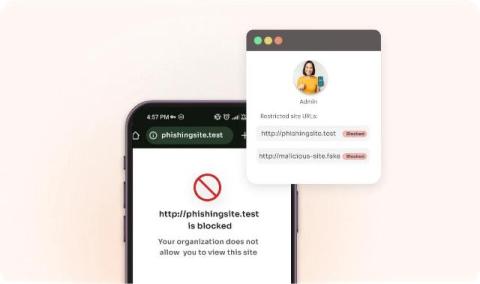
The bad news – if you’re wondering about the DORA compliance date, it already passed on January 17th 2025. The good news? If you’ve been too busy to even think about the EU’s Digital Operational Resilience Act, it’s not too late to score some quick compliance wins. This DORA compliance checklist is your blueprint for establishing not just compliance, but checks and balances for maintaining it.