Fake VS Code Extension on npm Spreads Multi-Stage Malware
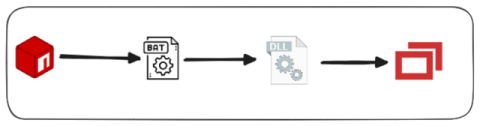
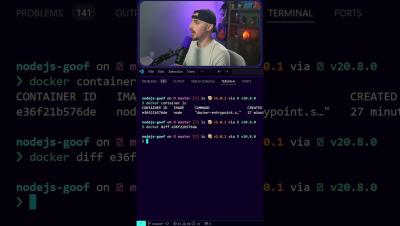
In a recent discovery, our research team uncovered a fake VS-code extension—truffelvscode—typosquatting the popular truffle for VS-code extension. This extension serves as a trojan horse for multi-stage malware. This blog takes a closer look at how the malicious extension operates, its obfuscation techniques, and IOCs related to this incident.