Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
September 2023
Cloudflare now uses post-quantum cryptography to talk to your origin server
Quantum computers pose a serious threat to security and privacy of the Internet: encrypted communication intercepted today can be decrypted in the future by a sufficiently advanced quantum computer. To counter this store-now/decrypt-later threat, cryptographers have been hard at work over the last decades proposing and vetting post-quantum cryptography (PQC), cryptography that’s designed to withstand attacks of quantum computers.
See what threats are lurking in your Office 365 with Cloudflare Email Retro Scan
We are now announcing the ability for Cloudflare customers to scan old messages within their Office 365 Inboxes for threats. This Retro Scan will let you look back seven days and see what threats your current email security tool has missed.
Detecting zero-days before zero-day
We are constantly researching ways to improve our products. For the Web Application Firewall (WAF), the goal is simple: keep customer web applications safe by building the best solution available on the market. In this blog post we talk about our approach and ongoing research into detecting novel web attack vectors in our WAF before they are seen by a security researcher. If you are interested in learning about our secret sauce, read on.
Encrypted Client Hello - the last puzzle piece to privacy
Today we are excited to announce a contribution to improving privacy for everyone on the Internet. Encrypted Client Hello, a new proposed standard that prevents networks from snooping on which websites a user is visiting, is now available on all Cloudflare plans. Encrypted Client Hello (ECH) is a successor to ESNI and masks the Server Name Indication (SNI) that is used to negotiate a TLS handshake.
Post-quantum cryptography goes GA
Over the last twelve months, we have been talking about the new baseline of encryption on the Internet: post-quantum cryptography. During Birthday Week last year we announced that our beta of Kyber was available for testing, and that Cloudflare Tunnel could be enabled with post-quantum cryptography. Earlier this year, we made our stance clear that this foundational technology should be available to everyone for free, forever.
Datadog Cloud Security Management: Unified Security and Observability
How Netskope's Security Competency and AWS Integrations Help Address the Shared Responsibility Model
It’s no secret that Amazon Web Services (AWS) continues to grow by leaps and bounds as organizations modernize their IT infrastructure by migrating apps and workloads to the cloud. And due to the AWS shared responsibility model of cloud security, a deep and broad ecosystem of security vendors has also grown up alongside AWS.
How to execute an Azure Cloud purple team exercise
Unlock the Power of Google Chronicle SIEM for Your Clients
Let's face it: Managing cybersecurity for multiple clients as an MSP can feel like navigating a maze, full of pitfalls and traps. Just when you think you have one security issue managed, another one pops up.
Amazon (AWS) S3 Bucket Take Over
Let’s try something a bit different and take a look at some of Trustwave SpiderLabs’ Open Source Intelligence (OSINT) research findings, and exploitation of vulnerable buckets and domains. I published this research internally on February 3, 2023, and here are my findings. Today, I will share with you how deleted S3 buckets could become a liability or threat to your organization and highlight the importance of cybersecurity in data and asset management.
Unparalleled Cloud Visibility in Action with Sysdig's Enhanced Searchable Inventory
Customer Corner: "How BigCommerce Achieved Real-Time Cloud Security"
Rethinking Cloud Security with Sysdig's CNAPP
New Study Reveals Cloud Giants are Holding Businesses Captive
Welcome to connectivity cloud: the modern way to connect and protect your clouds, networks, applications and users
The best part of our job is the time we spend talking to Cloudflare customers. We always learn something new and interesting about their IT and security challenges. In recent years, something about those conversations has changed. More and more, the biggest challenge customers tell us about isn’t something that’s easy to define. And it’s definitely not something you can address with an individual product or feature.
Cloudflare One - Secure Web Gateway
Ensuring vendor integrity: Why the cloud shouldn't be your only backup
As a senior consultant I deal with customers across numerous industries and maturity levels. I am often engaged in conducting risk assessments or gap analysis aligned with common frameworks such as the National Institute for Standards and Technology’s (NIST) Cybersecurity Framework (CSF). Most, if not all, the frameworks have a few controls that focus on the organization’s backup processes and disaster recovery plans.
Cloudflare account permissions, how to use them, and best practices
In the dynamic landscape of modern web applications and organizations, access control is critical. Defining who can do what within your Cloudflare account ensures security and efficient workflow management.
Ensuring Compliance in an Ever-Evolving Cloud Security Landscape
According to CSO the fines incurred for data breaches or non-compliance with security and privacy laws, for only a handful of companies, has cost $4.4 billion. The global average cost of a data breach in 2023 was $4.45 million, a 15% increase over 3 years (IBM). The challenge for organizations is how to safeguard sensitive information while adhering to the law, but without compromising innovation. Cyber threats loom large, affecting businesses in every industry.
Secrets Management Best Practices: Secure Cloud-native Development Series
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the fifth and final part of the series, and it will teach you to handle credentials and secrets management best practices for securing cloud-native applications. Every organization has their way of managing credentials. In the past, with legacy application architectures, this was a bit more manual and arduous.
How to Secure Remote Workers and Cloud Access at the Same Time
Typo traps: analyzing traffic to exmaple.com (or is it example.com?)
A typo is one of those common mistakes with unpredictable results when it comes to the Internet’s domain names (DNS). In this blog post we’re going to analyze traffic for exmaple.com, and see how a very simple human error ends up creating unintentional traffic on the Internet. Cloudflare has owned exmaple.com for a few years now, but don’t confuse it with example.com!
Move to the Cloud with Confidence: 6 Key Risks & Mitigation Techniques - Part 2
According to Gartner, cloud spending will reach $597.3 billion by the end of 2023. Whether it’s infrastructure as a service (IaaS), a software as a service cloud application (SaaS), or some other use for the cloud, organizations are finally adopting cloud use models that help increase scalability, reliability, and speed, while reducing overhead costs.
Securing RDS with Teleport
Analyzing EKS cluster data with Calico and SIEM to detect threats and improve security
Security Information and Event Management (SIEM) is essential for enterprise organizations because it provides the tools and capabilities needed to effectively monitor, detect, respond to, and mitigate cybersecurity threats, while also supporting compliance and overall security strategy enhancement.
Cloudflare Email Security now works with CrowdStrike Falcon LogScale
We are excited to announce an extended partnership between CrowdStrike and Cloudflare to bring together Cloudflare Email Security and CrowdStrike Falcon® LogScale. With this integration, joint customers who have both Falcon LogScale and Cloudflare Email Security can now send detection data to be ingested and displayed within their Falcon LogScale dashboard.
Cloud Data Protection: How 5 Organizations Stay Secure With Lookout
SaaS applications like Microsoft 365, Google Workspace, and Salesforce are now a ubiquitous part of business. With so much corporate data now residing in the cloud, a perimeter-based approach to security doesn’t cut it. To enforce cloud data protection policies across SaaS apps, a cloud access security broker (CASB) has become a necessity.
AWS and Mend.io Webinar: Five Principles of Modern Application Security Programs
The confluence of cloud and AI: charting a secure path in the age of intelligent innovation
The fusion of Cloud and AI is more than just a technological advancement; it’s a paradigm shift. As businesses harness the combined power of these transformative technologies, the importance of a security-centric approach becomes increasingly evident. This exploration delves deeper into the strategic significance of navigating the Cloud-AI nexus with a focus on security and innovation.
From one realm to another: Ensuring data protection in a cloud migration
In today's digital landscape, businesses are embracing the transformative power of cloud migration. Shifting operations from on-premises systems to cloud environments promises unprecedented benefits in scalability, cost-efficiency, and agility.
CrowdStrike to Acquire Bionic to Extend Cloud Security Leadership with Industry's Most Complete Code-to-Runtime Cybersecurity Platform
I’m excited to share that today at Fal.Con, CrowdStrike announced it has agreed to acquire Bionic, a pioneer of application security posture management (ASPM). This will give our customers the most seamless and comprehensive view of cloud risk — from code development through runtime — in a single, unified platform.
AWS's Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation
The Sysdig Threat Research Team (TRT) has uncovered a novel cloud-native cryptojacking operation which they’ve named AMBERSQUID. This operation leverages AWS services not commonly used by attackers, such as AWS Amplify, AWS Fargate, and Amazon SageMaker. The uncommon nature of these services means that they are often overlooked from a security perspective, and the AMBERSQUID operation can cost victims more than $10,000/day.
Jit is live on AWS! Sneak peek Episode 1 - 12-09-2023
4 Best Practices to Guarantee Successful AWS Migration
Successful AWS migration takes more than simply choosing to migrate. It’s a journey, and you need to be confident in your choice to upend your existing on-premise workflows to align with your business’s future. The fundamental process around a migration strategy includes understanding the benefits of a new system, assessing gaps in your existing system, migration planning, and ultimately the actual migration aspect.
10 Cloud Security Best Practices to Memorize
One thing the IT security community should be recognized for is its willingness to share information and solutions. If you’re moving to the cloud — or interested in increasing your applications’ security, take advantage of that.
Unlock the Power of the Cloud for your Industry: A Comprehensive Guide to Cloud Migration
Navigate Your Hybrid Cloud Journey with Opti9
Demo - Train Your Own Classifier
NIST Cloud Security: Standards, Best Practices, & Benefits
Latest cloud security statistics reveal that 91% of all organizations have some portion of their IT environment hosted in cloud platforms. While cloud computing comes with many benefits, companies have trouble scaling up the security to meet the data and privacy challenges posed by it.
Making Content Security Policies (CSPs) easy with Page Shield
Modern web applications are complex, often loading JavaScript libraries from tens of different sources and submitting data to just as many. This leads to a vast attack surface area and many attack types that hackers may leverage to target the user browser directly. Magecart, a category of supply chain attack, is a good example.
Cloudflare One for Secure Access
How To Conduct An Azure Security Audit: The Actionable Guide
Over 56% of organizations globally use Microsoft Azure for their cloud services owing to its convenience, cost-effectiveness, and scalability. It is vital to secure your Azure environment against the backdrop of an ever-evolving threat landscape. Otherwise, your database and digital assets can leak sensitive data. And one way to do it is through Azure security audits.
Move to the Cloud with Confidence: 6 Key Risks & Mitigation Techniques, Part 1
Over the past several years, an increasingly fluid work environment has followed trends of modern globalization in the workplace. Leveraging cloud solutions, many companies have let go of historical limitations imposed by on-premises and local solutions. The truth is, cloud outsourcing can be a game changer, as it provides organizations with more cost effective and management friendly software, infrastructure, and computing power than would otherwise be possible.
AWS Security Data Lake and the Devo Platform
In the ever-evolving cybersecurity landscape, the need for a comprehensive security data lake (SDL) has become important to some enterprises. Organizations face multi-vector threats that demand extensive data analysis to effectively counter them.
What Are the Most Common Security Risks of Cloud Computing?
Identifying and understanding the most common cloud security risks is crucial to a successful cloud computing adoption strategy. Organizations migrating to the cloud continually face new threats and discover vulnerabilities that were not present when they operated software deployed on-premises. According to IBM’s Cost of a Data Breach report, almost half of all data breaches are happening in the cloud, with attacks on systems hosted on public clouds costing an average of $5.02 million.
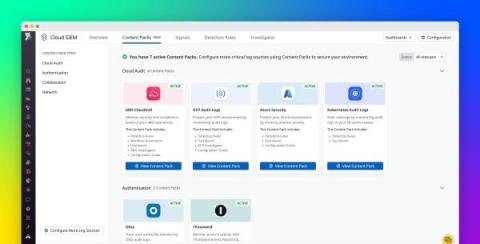
Easily ingest and monitor security logs with Cloud SIEM Content Packs
Datadog Cloud SIEM helps customers protect their cloud environment and SaaS applications against threats with built-in threat detection rules, interactive dashboards, workflow blueprints, and in-depth support resources. These capabilities provide valuable insights into your security posture, so you can respond promptly to emerging threats. In order to generate these insights, Cloud SIEM analyzes log data, which users can start sending to Datadog by enabling one of our out-of-the-box integrations.
Best in Class
Why AWS indeed. This is not one of those start with why posts, but hopefully a peek into the reasons behind our partnership with AWS and what that means for you and how it could benefit you. The beginnings of something great Public cloud is well established, with about 50% of all workloads now running in a public cloud location. We have heard of ”the big three” cloud providers: AWS, Azure, and Google Cloud.
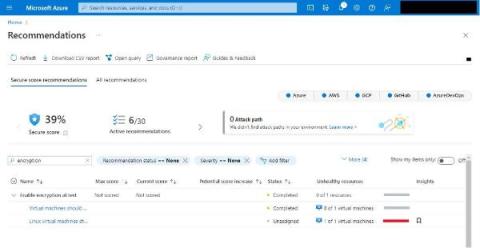
Easily Enable Encryption: Secure Cloud-native Development Series
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the fourth part of the series, and it will teach you why and how to easily enable encryption and save yourself headaches down the road. Here's a new motto: encrypt everything! When securely moving to cloud-native technologies, building encryption in from the start will save us a lot of headaches later.
How To Write A Post-Audit Cloud Security Report
A post-audit cloud security report is a document that provides an overview of the security status of the cloud environment, infrastructure, and applications of a business. It verifies that vulnerabilities and security flaws have been identified and assessed, and offers recommendations to address these security gaps.
Penetration Testing In AWS - A DIY Guide For Beginners
Penetration Testing, often referred to as 'pen testing' or 'ethical hacking', is a practice wherein a simulated cyber attack is launched against your own computer system. The objective is to unearth vulnerabilities before malicious hackers do and fix them promptly to bolster your security stance.
A Comprehensive Guide to Azure Data Security
In our interconnected world, the value of data is growing with cyber threats also on the rise. This causes the security and protection of data to become crucial. Organizations have become compelled to adopt strict measures to safeguard their data. Implementing security practices in data protection and encryption ensures the confidentiality, integrity, and availability of the data stored in the cloud.
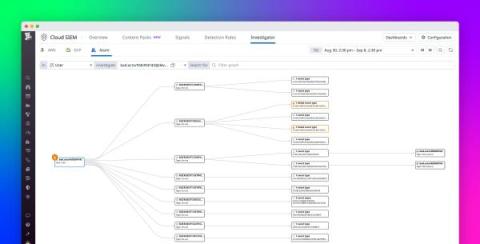
Visualize activity in your Azure environment with Datadog Cloud SIEM Investigator
Cloud infrastructures can comprise thousands of interconnected and dynamic resources. This complexity introduces unique challenges to monitoring and securing these architectures. Understanding where user activity originates—and what actions constitute security threats—is a complex task when you’re dealing with the huge volume of logs, metrics, and other telemetry that highly distributed cloud environments generate each day.
Lookout Cloud Security Platform: Free Your Hybrid Workforce
Context Defines Next Gen SWG
Entitle Joins AWS Marketplace
We're thrilled to announce that starting this week, Entitle has made its debut on the prestigious AWS Marketplace. This is a significant milestone that promises to improve cloud access management for AWS customers.
Improve visibility and identify risk across your Google Cloud environments with AlgoSec CloudFlow
With expertise in data management, search algorithms, and AI, Google has created a cloud platform that excels in both performance and efficiency. The advanced machine learning, global infrastructure, and comprehensive suite of services available in Google Cloud demonstrates Google’s commitment to innovation. Many companies are leveraging these capabilities to explore new possibilities and achieve remarkable outcomes in the cloud.
Life in the Clouds: Navigating Security Challenges in Cloud Environments
As the realm of technology continues to evolve, the significance of cloud computing has grown exponentially. This paradigm shift offers unparalleled scalability, efficiency, and cost-effectiveness benefits. However, with these advantages come a host of security challenges that need careful consideration. This article delves into the vital realm of cloud security, exploring the multifaceted landscape of safeguarding data, identities, networks, and services.
How to Solve the Cloud vs On-Premise Security Dilemma
Organizations need to protect themselves from the risks of running their business over the internet and processing sensitive data in the cloud. The growth of SaaS applications, Shadow IT and work from anywhere have therefore driven a rapid adoption of cloud-delivered cybersecurity services. Gartner defined SSE as a collection of cloud-delivered security functions: SWG, CASB, DLP and ZTNA. SSE solutions help to move branch security to the cloud in a flexible, cost-effective and easy-to-manage way.
How to get AWS FTR approved with Jit security
Building a cloud-based financial app with regulatory compliance
How to Support Business Agility With Hybrid Cloud Services
Hybrid cloud takes the capabilities of the public and various private cloud options and merges them, allowing businesses to host different workloads within different environments depending on their performance, security, and resource needs. Companies leveraging a hybrid cloud strategy promote business competitiveness and agility, allowing them to respond to changes in resource demands quickly.
Elevate load balancing with Private IPs and Cloudflare Tunnels: a secure path to efficient traffic distribution
In the dynamic world of modern applications, efficient load balancing plays a pivotal role in delivering exceptional user experiences. Customers commonly leverage load balancing, so they can efficiently use their existing infrastructure resources in the best way possible. Though, load balancing is not a ‘one-size-fits-all, out of the box’ solution for everyone.
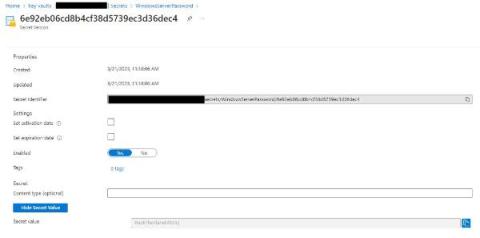
Handling Secrets with AWS Secrets Manager
This tutorial helps you better understand AWS Secrets Manager, how it works under the hood and how to access it from Kubernetes clusters.
Cloudflare announces unified Data Protection Suite to address the risks of modern coding and increased AI use
What's next for Cloudflare One's data protection suite
Today, we announced Cloudflare One for Data Protection — a unified suite to protect data everywhere across web, SaaS, and private applications. This suite converges capabilities including our data loss prevention (DLP), cloud access security broker (CASB), Zero Trust network access (ZTNA), secure web gateway (SWG), remote browser isolation (RBI), and cloud email security services. The suite is available and packaged now as part of Cloudflare One, our SASE platform.
Cloudflare One for Data Protection
Data continues to explode in volume, variety, and velocity, and security teams at organizations of all sizes are challenged to keep up. Businesses face escalating risks posed by varied SaaS environments, the emergence of generative artificial intelligence (AI) tools, and the exposure and theft of valuable source code continues to keep CISOs and Data Officers up at night.
Cloudflare One for Data Protection Demo
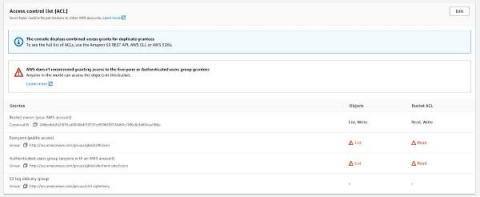
A Bucket of Phish: Attackers Shift Tactics with Cloudflare R2 Public Buckets
In our previous blog, we found a lot of phishing and scam URLs abusing Cloudflare services using pages.dev and workers.dev domains, respectively. We’re now seeing a lot of phishing emails with URLs abusing another Cloudflare service which is r2.dev.
Securing Cloud-Native Environments: Containerized Applications, Serverless Architectures, and Microservices
Enterprises are embracing cloud platforms to drive innovation, enhance operational efficiency, and gain a competitive edge. Cloud services provided by industry giants like Google Cloud Platform (GCP), Azure, AWS, IBM, and Oracle offer scalability, flexibility, and cost-effectiveness that make them an attractive choice for businesses. One of the significant trends in cloud-native application development is the adoption of containerized applications, serverless architectures, and microservices.
Why Companies Are Migrating To AWS With a Trusted Partner
If you’re reading this article, you’re likely already considering an AWS migration for your company. You already have a handle on some of the perks migrating to AWS can have on your business but are reluctant considering how much disruption nearly every industry experienced within the last year or more. Rather than opting for more change, you might consider holding on to what you know until this period of disruption comes to an end.
Managing Storage Access: Secure Cloud-native Development Series
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the third part of the series, and it will teach you how to secure cloud storage and handle access controls on S3 buckets. Each cloud provider has managed storage services that your organization is already probably utilizing.
Webinar - Securing your Cloud Infrastructure with AWS & Tines
4 Cloud Security Best Practices for Protecting SaaS Apps
In today's rapidly evolving technological landscape, SaaS applications have been essential in driving efficiency and promoting collaboration. But the benefits of the cloud also bring new risks, and securing your organization against a vast array of cloud security threats can be a unique challenge.
WatchGuard Wins Cloud Computing Security Excellence Award
Today, we are delighted to share that WatchGuard has been named a winner in the Cloud Computing Magazine’s 2023 Cloud Computing Security Excellence Awards! This prestigious awards program recognizes companies that have most effectively leveraged Cloud computing in their efforts to bring new, differentiated offerings to the market.
Top 7 Azure security assessment tools
Azure security refers to the safeguards implemented by Microsoft Azure to protect the information and services hosted on its cloud platform. Azure security offers a safe environment for using cloud services, storing data, and executing applications, assisting enterprises in meeting regulatory requirements. Azure security assessment tools test your cloud architecture to find data and identify hazards, their potential effects, and their likelihood of occurring.
What is cloud app security?
“Cloud App Security” refers to a collection of tools developed to improve the safety of cloud-based software and services. With the increasing usage of cloud computing, it is more important than ever for organizations to take measures to keep their data and users secure.