Security SOS: It's dangerous to view cloud and data separately
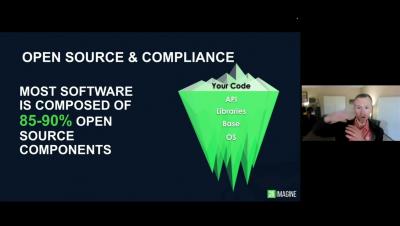
Security risks within the IT infrastructure of global businesses are increasingly prevalent – and damaging. When swathes of data are separated in the hybrid or multi cloud, it can leave big open doorways for malware to walk right in. The message I want businesses to hear is that cloud and data are not separate. IT only exists to service the needs of a business’ data. Securing cloud services – and therefore your data – is a business-critical issue.