Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Why Managed Detection and Response is a Key Component to any Security Plan
The overnight move to remote and hybrid work models instantly created a more complex infrastructure for many organizations as they shifted their workers from corporate offices to their homes. The threat surface expanded exponentially as devices moved off-prem and into potentially unsecured environments and grew again as workers added their own devices to the mix.
Understanding Suspicious User Types With UEBA
The cybersecurity threat landscape is evolving rapidly. Hackers and other malicious users are becoming increasingly sophisticated in their attack methods, rendering traditional security tools obsolete. Modern cybercriminals will use any means to break into firewalls, send emails with infected attachments, or even bribe employees to share login credentials. Businesses in all industries must identify and implement comprehensive IT security tools and strategies to protect their valuable assets.
Explore Corelight evidence in Humio Community Edition
Now available: A free and easy way to learn about Humio and Corelight. As part of our alliance partnership with CrowdStrike and Humio, Corelight is excited to announce a new collaboration that allows our customers and the community to experience the value of evidence.
Weaponizing paranoia: developing a threat detection strategy
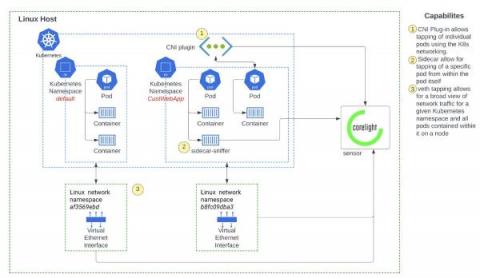
Deeper visibility into Kubernetes environments with network monitoring
Network monitoring solutions can overcome the security visibility blind spots in Kubernetes environments, by providing a source of truth for SOC analysts. Container security solutions broadly span the spectrum of (a) prevention - securing the container image and ensuring the right policies are in place during runtime and (b) detection - monitoring runtime events for threat detection and investigation.
The role of Threat Intelligence Platforms in Implementing Extended Detection and Response
As the new year continues to unfold, cybersecurity budget holders will be deep into the process of identifying where to allocate funds to best enhance protection against cyberthreats. The good news is that budgets are rising, with industry commentators frequently reporting that companies are committing more money to strengthening their posture against persistent and sophisticated threats.
CrowdStrike and Mandiant Form Mission-Focused Strategic Partnership to Protect Organizations Against Cyber Threats
Don't trust. Verify with evidence.
What matters most in a criminal trial? Evidence. Everything depends on the quality and depth of facts deployed to build a case for innocence or guilt. Without compelling evidence, no jury can draw accurate conclusions.
Understanding cloud security
Discover how to manage cloud permissions and configurations, detect threats in the cloud, and apply a unified approach for cloud and container threat detection.