Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Securing SSH on EC2: What are the real threats?
Every compliance audit will ask you to secure SSH, and every time a scanner checks the configuration or CSPM of your cloud account you’ll be warned for it. For example, if you don’t secure SSH on EC2, you’ll certainly get a critical alert stating that one of your Security Groups has its SSH port (22) open to the world. When this happens, you may think: Have I been pwned?
With Trustwave, the Best in MDR Just Got Better
Trustwave has recreated new Managed Detection and Response (MDR) services to deliver unmatched capabilities tailored to fit an organization regardless of size or budget. While larger organizations may have the resources for heavy security investments, small and medium enterprises (SME) often struggle to keep up with this punishing pace and finding enough qualified security personnel can be even more challenging with the ongoing skills shortage.
Enhanced Network Evidence for the Modern SOC
CrowdStrike Introduces CrowdStrike Asset Graph to Help Organizations Proactively Identify and Eliminate Blind Spots Across Attack Surface
CrowdStrike Adds Strategic Partners to CrowdXDR Alliance and Expands Falcon XDR Capabilities to Supercharge Threat Detection, Investigation, Response and Hunting
RSAC 2022: CrowdStrike Delivers Protection that Powers Productivity
The theme of RSA Conference 2022 succinctly captures the aftermath of the disruption we’ve all experienced over the last couple of years: Transform. Customers continue to transform and accelerate digital initiatives in response to the massive economic and technological shifts driven by the COVID-19 pandemic.
Forescout and Cysiv: Threat Detection Across Your Digital Terrain
Today marks an exciting moment in time for our customers and partners. Today, Forescout announced its intent to acquire Cysiv, a company with deep expertise in data-powered threat detection and response.
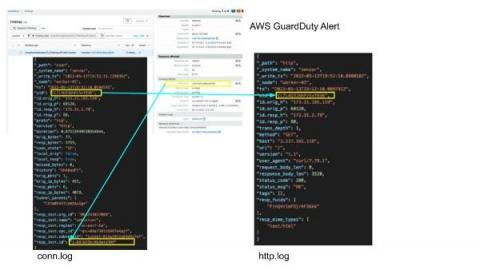
Enriching NDR logs with context
In this post, we show how enriching Zeek® logs with cloud and container context makes it much faster to tie interesting activity to the container or cloud asset involved.In cloud or container environments, layer 3 networking is abstracted away from the higher-level tasks of running workloads or presenting data. Because of this abstraction, when Zeek logs are collected for cloud or container network environments, the attribution of a network flow to actual workload or application is difficult.
CrowdStrike Falcon Identity Threat Protection Added to GovCloud-1 to Help Meet Government Mandates for Identity Security and Zero Trust
CrowdStrike recently announced the addition of Falcon Identity Threat Protection and Falcon Identity Threat Detection to its GovCloud-1 environment, making both available to U.S. public sector organizations that require Federal Risk and Authorization Management Program (FedRAMP) Moderate or Impact Level 4 (IL-4) authorization. This includes U.S. federal agencies, U.S. state and local governments and the Defense Industrial Base (DIB).