Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
The future of email threat detection
As businesses continue to adopt cloud integration and remote work increases, security teams are facing more visibility challenges as well as an influx of security event data. There is more need to understand the threats than ever before, as the threat surface area increases, and tactics increase. Cyber threats are becoming more sophisticated and occurring more frequently, forcing organizations to rely on quality threat detection to protect their data, employees, and reputation.
The best cybersecurity defense is great evidence
The saying “data is king” has been around for quite a while and we all know that the world operates and makes decisions on digital data 24x7x365. But, is data king in the field of cybersecurity? I believe that evidence - not data - is what is needed to speed defenders’ knowledge and response capabilities, so let's talk about both.
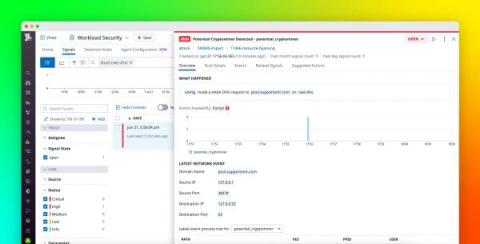
Identify security vulnerabilities with DNS-based threat detection
The Domain Name System (DNS) is responsible for mapping client-facing domain names to their corresponding IP addresses, making it a fundamental element of the internet. DNS-level events provide valuable information about network traffic that can be used to identify malicious activity. For instance, monitoring DNS lookups can help you see whether a host on your network attempted to connect to a site known to contain malware.
How CrowdStrike's Machine Learning Model Automation Uses the Cloud to Maximize Detection Efficacy
At CrowdStrike, we combine cloud scale with machine learning expertise to improve the efficacy of our machine learning models. One method for achieving that involves scanning massive numbers of files that we may not even have in our sample collections before we release our machine learning models. This prerelease scan allows us to maximize the efficacy of our machine learning models while minimizing negative impact of new or updated model releases.
Spotlight on Technology - Managed Detection & Response
The evidence bank: leveraging security's most valuable asset
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control. Evidence can also be used reactively by supporting detection (re)engineering, response, and recovery activities, guiding us back to identifying and protecting structural risks.
Automating Detection-as-Code
In cybersecurity, there has been a shift to adopt more software development principles in order to create security solutions quickly and reliably. Utilization of tools like Git and Continuous Integration/Continuous Deployment (CICD) pipelines have become more common to achieve reliable deployments. At Tines, while we strive to make automation accessible to anyone without development skills, our platform is also highly flexible to accommodate developer-centric uses.
Staying Connected with Cloud Exchange: Netskope Cloud Threat Exchange & Digital Shadows Plugin
Many technology professionals have experienced the sense of frustration that occurs when multiple tools in their environment do not play nicely with each other. When technology leaders are making decisions about bringing new tools into their environment, they should be thinking about more than whether the platform is just a shiny new object that adds a new capability to their team.
5 Reasons Why Managed Detection and Response (MDR) Must be on Every Company's Security Roadmap
The Managed Detection and Response (MDR) solutions offered by security firms today are a far cry from those first deployed by vendors. To better understand how MDR has grown over the years and the changes Trustwave has implemented to stay ahead of the curve, we spoke with Trustwave's Jesse Emerson, Vice President, Solution Architecture & Engineering.