Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Detecting CVE-2022-26937 with Zeek
This month, Microsoft announced a vulnerability in NFS. The exploit lies in how an attacker can force a victim NFS server to request an address from the attacker’s fake NFS server. The address returned will overflow memory on the victim NFS server and cause a crash. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof-of-concept exploit for this vulnerability and wrote a Zeek®-based detection for it. You can find a PCAP of this exploit in our GitHub repository.
Detecting CVE-2022-23270 in PPTP
This month, Microsoft announced a vulnerability in PPTP, a part of the VPN remote access services on Windows systems that runs on port 1723/tcp. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof of concept exploit for this vulnerability and wrote a Zeek®-based detection for it.
Corelight Investigator accelerates threat hunting
This morning we announced Corelight Investigator, an open NDR platform that enables security teams with the next-level evidence they need to disrupt attacks and accelerate threat hunting through an easy-to-use, quick-to-deploy SaaS solution. How does it work? Investigator combines battle-tested network evidence with intelligent alert scoring to deliver prioritized alerts tied to correlated evidence, enabling analysts to cut through the queue and accelerate incident response.
Corelight Investigator
Finding CVE-2022-22954 with Zeek
CISA released a warning to federal agencies on May 18 that APT actors are actively exploiting recent vulnerabilities found in VMware, including CVE-2022-22954. Your first thought may have been to want new signatures, indicators, and/or behavioral techniques to detect attempted and successful exploits. If you’re a Zeek user or Corelight customer, you’ll find that sometimes you’re already getting what you need.
What makes evidence uniquely valuable?
American novelist F. Scott Fitzgerald famously wrote that “the test of a first-rate intelligence is the ability to hold two opposing ideas in mind at the same time, and still retain the ability to function.” All experienced security practitioners learn to master this mental trick. On the one hand, they believe efforts to prevent and detect breaches will be effective. On the other hand, they diligently prepare for the day when their efforts will fail.
EASM: Is it late to the party?
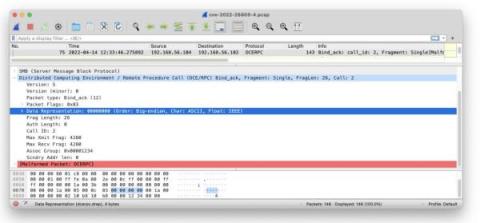
Another day, another DCE/RPC RCE
CVE-2022-26809 was patched in Microsoft’s previous Patch Tuesday (April 12) and it’s a doozy: remote code execution on affected versions of DCE/RPC hosts. The vulnerability attracted a lot of attention in the security community, both because of its severity but also because it appears to be really hard to trigger.