Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Know your environment: Tenable/Corelight integration for prioritized IDS alerts
One of the major causes of alert fatigue for SOCs is a class of alerts that fall in between false positives and useful detections: when an actual attack has been launched, and the detection is working correctly, but the host on the receiving end is not vulnerable, guaranteeing that the attack will fail.
Real-Time Threat Detection in the Cloud
Organizations have moved business-critical apps to the cloud and attackers have followed. 2020 was a tipping point; the first year where we saw more cloud asset breaches and incidents than on-premises ones. We know bad actors are out there; if you’re operating in the cloud, how are you detecting threats? Cloud is different. Services are no longer confined in a single place with one way in or one way out.
One SIEM is not enough?
The idea behind the SIEM (and now XDR!) technologies was to provide a single engine at the heart of the SOC, aggregating data, enabling analytics and powering workflow automation. The SIEM would act as one place to train analysts and integrate a range of complementary technologies and processes. Given the efficiency that comes from centralization, I was surprised to hear that a growing number of defenders are actually using two SIEMs. Why is that?
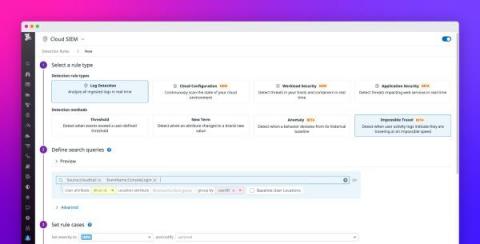
Detect suspicious login activity with impossible travel detection rules
Many modern applications are regularly accessed by countless users from all over the world, which makes it difficult to identify anomalous patterns in login activity indicative of a security breach. This challenge is compounded by the fact that people travel often and regularly access their accounts from new locations. To detect this common attack vector, the Datadog Cloud SIEM now provides the impossible travel detection rule type which helps you spot suspicious logins with confidence.
Reinventing Managed Detection and Response (MDR) with Identity Threat Protection
The modern threat landscape continues to evolve with an increase in attacks leveraging compromised credentials. An attacker with compromised credentials too frequently has free reign to move about an organization and carefully plan their attack before they strike. This week Falcon Complete™, CrowdStrike’s leading managed detection and response (MDR) service, announced a new managed service capability that once again sets the standard for MDR.
Log4j: Separating the exploits from the noise
Acting on CISA's advice for detecting Russian cyberattacks
Given that active cyber warfare has broken out alongside Russia’s active invasion of Ukraine - from Russian wiper malware to Anonymous hacking Russian state TV - CISA’s recent “Shields Up” memo is a timely insight into some of the TTPs defenders of critical infrastructure should be keeping an eye out for. Let’s break down the four key areas outlined in the memo and examine ways they can be detected with network data.