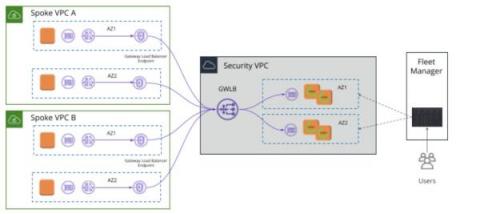
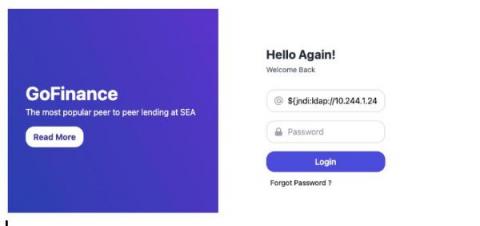
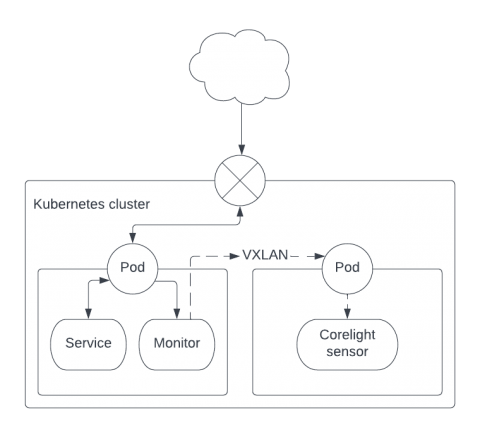
Elastic and Tines partner to detect security threats and reduce mean time to respond
Today, we’re happy to announce that Elastic and Tines are partnering to help our joint users detect security threats and reduce mean time to respond. Many of the world’s best security teams rely on the power of Elastic’s high-speed, cloud-scale detection, prevention, and response capabilities to investigate and contain potential security threats within their environments.