Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Introducing ATT&CK Detections Collector
The Splunk SURGe team loves to automate and simplify mundane tasks. Through rapid response blogs, we provide context and analysis on late breaking security events that affect everyone, not just Splunk customers. We are firm believers that through shared knowledge and experience we can help the masses better understand the threat landscape and how they can improve their security posture.
Security strategy for the next Log4Shell
Last week I had the privilege to be in Washington, DC talking to a group of defenders. I heard a clear pattern of words: “data-driven,” “telemetry-first,” and “visibility”.
A Review of Log4Shell Detection Methods
Ever since the public exploit of the Log4Shell remote code execution (RCE) vulnerability became known on December 10, 2021, security teams have been scrambling to understand the risk to their environments. Part of that scramble has been to ascertain which tools are best positioned to help detect the vulnerability. Which approaches are most effective and where do they fall short?
CrowdStrike Adds New Strategic Partners to Groundbreaking CrowdXDR Alliance
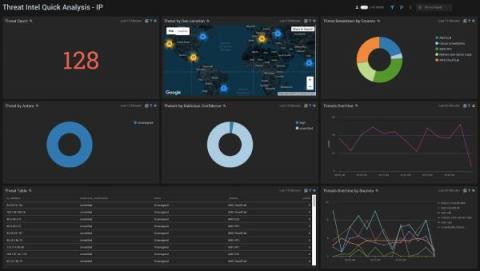
Detecting Log4j exploits via Zeek when Java downloads Java
We have published an initial blog on the Log4j exploit and a followup blog with a second detection method for detecting the first stage of exploits occurring over LDAP. Today, we will discuss a third detection method, this one focused on the second-stage download that happens after the first stage completes. In this case, the JVM will download additional Java code payloads over HTTP.
CrowdStrike APAC Named Frost & Sullivan Endpoint Security Industry Company of the Year and was also recognized as a Customers' Choice by Gartner
Arctic Wolf Cloud Detection and Response
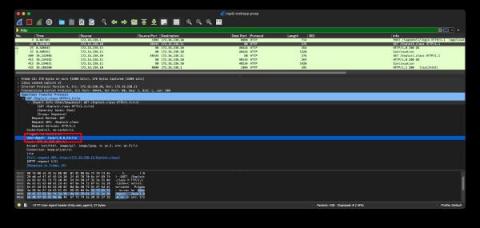
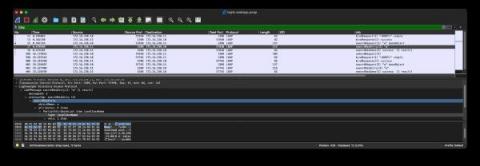
Detecting Log4j via Zeek & LDAP traffic
We recently discussed some methods for detecting the Log4j exploit, and we’ve now developed another method that everyone running Zeek® or a Corelight sensor can use. Our new approach is based on the rarity of legitimate downloads of Java via LDAP. Zeek does not currently have a native LDAP protocol analyzer (though one is available if you are running Spicy). This will not stop you from detecting this exploit downloading Java over LDAP, though. To see how, read on.