Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Torq's No-Code Security Automation Solution Now Available in AWS Marketplace
Policy as Code with Azure API Management (APIM) and OPA
A common use case for Open Policy Agent (OPA) is to decouple authorization from the application. This enables policies and decisions to be managed centrally and lifecycled independently to the application. For application use cases, OPA can be integrated at the API Gateway, Service Mesh or Microservices layer or any combination of these.
Mobile Device Forensics: Challenges, Threats, & Solutions
Mobile forensics is the process of accessing, recovering, and analyzing digital evidence from mobile devices using a court accepted methodology. The information that can be gleaned from a criminal’s phone is highly valuable. That’s why mobile forensics and digital forensics as a whole are valuable assets for law enforcement and intelligence agencies worldwide.
Datadog Cloud Security Management Demo
Must Know Approaches for Maintaining Mobile Application Security and CIA Traits
Nowadays, every business wants to reach out to a larger audience. And the best way for it is Mobile App Development. Whether someone is at work, at home, or somewhere outside, people frequently go through apps on their mobiles. Such apps collect data, store it and process it to provide reliable results. Indeed, our sensitive and confidential data is also getting into the same process. Hence, it makes a top priority to focus on mobile application security.
80% of companies experience security incidents in the Cloud
Migrating to the Cloud brings many advantages for companies. First of all, they reduce their operating costs by almost 40%. They also increase their agility, reduce the maintenance time of traditional IT infrastructures, and gain flexibility and scalability. However, as the number of workloads deployed in the Cloud grows, more and more organizations are struggling to keep pace with security requirements.
Automating RDS Security Via Boto3 (AWS API)
When it comes to security in AWS, there is the shared responsibility model for AWS services, which is divided into AWS responsibility ‘security of the cloud’ and customer responsibility ‘security in the cloud’. For more detail on this please check the shared-responsibility-model. Figure 1: AWS Shared Responsibility Model Source: shared-responsibility-model.
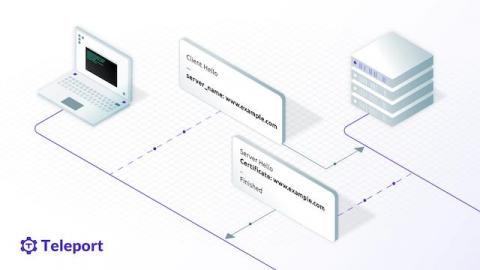
TLS Routing Support for Teleport Behind an AWS Application Load Balancer
In Teleport 8, we introduced the TLS Routing feature that can multiplex all client connections on a single TLS/SSL port. Recently we've added support for TLS Routing for Database Access when Teleport is deployed behind an AWS Application Load Balancer (ALB). In this article, we will take a deep look at the problem with Teleport behind an ALB and how we solved it.
Best practices for endpoint security in cloud-native environments
Editor’s note: This is Part 2 of a five-part cloud security series that will cover protecting an organization’s network perimeter, endpoints, application code, sensitive data, and service and user accounts from threats.