Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
4 Cloud Security Best Practices for Protecting SaaS Apps
In today's rapidly evolving technological landscape, SaaS applications have been essential in driving efficiency and promoting collaboration. But the benefits of the cloud also bring new risks, and securing your organization against a vast array of cloud security threats can be a unique challenge.
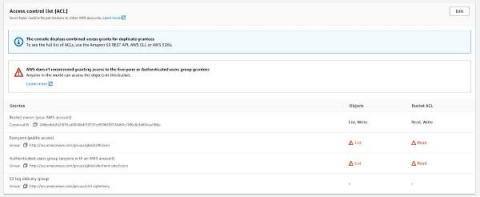
Managing Storage Access: Secure Cloud-native Development Series
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the third part of the series, and it will teach you how to secure cloud storage and handle access controls on S3 buckets. Each cloud provider has managed storage services that your organization is already probably utilizing.
Cybersecurity Secrets: How AI Keeps Us Safe
Random but Memorable - Episode 11.3: Teach Bot Cybersecurity Recipes with Clint Bodungen
Reading Made Mobile: Step-by-Step Guide to Access Z Library on Your Phone for Free
WatchGuard Wins Cloud Computing Security Excellence Award
Today, we are delighted to share that WatchGuard has been named a winner in the Cloud Computing Magazine’s 2023 Cloud Computing Security Excellence Awards! This prestigious awards program recognizes companies that have most effectively leveraged Cloud computing in their efforts to bring new, differentiated offerings to the market.
Top 7 Azure security assessment tools
Azure security refers to the safeguards implemented by Microsoft Azure to protect the information and services hosted on its cloud platform. Azure security offers a safe environment for using cloud services, storing data, and executing applications, assisting enterprises in meeting regulatory requirements. Azure security assessment tools test your cloud architecture to find data and identify hazards, their potential effects, and their likelihood of occurring.
What is cloud app security?
“Cloud App Security” refers to a collection of tools developed to improve the safety of cloud-based software and services. With the increasing usage of cloud computing, it is more important than ever for organizations to take measures to keep their data and users secure.