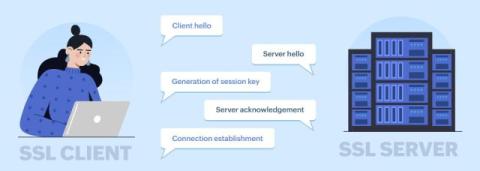
Mastering Sales Funnel Management and B2B Lead Generation Solutions
In today's competitive business environment, achieving consistent revenue growth requires a strategic approach to converting potential customers into loyal clients. Two essential components of this strategy are effective sales funnel management and implementing robust B2B lead generation solutions. Together, these practices enable businesses to optimize the customer journey, attract high-quality leads, and maximize conversions.