|
By Kovrr
As digital threats grow more sophisticated and cyber regulations expand in scope, business stakeholders are beginning to recognize the need to learn more about cybersecurity and how it impacts organizational performance. With this recognition comes the elevation of chief information security officers (CISOs) into the boardroom, tasked with explaining these cyber intricacies and offering strategies that can help safeguard operational resilience and drive long-term growth.
|
By Kovrr
A little over a year ago, the US SEC’s rules on cybersecurity incident disclosures were enacted, mandating that all publicly traded companies report material cyber events within four days after they had been determined as such unless exempted for national security or safety reasons. The rationale behind these rulings was that they would provide investors and relevant stakeholders with the information necessary to make more informed decisions, thereby leading to more realistically priced options.
|
By Kovrr
Managing risk is not an isolated process; it involves a series of coordinated efforts, sometimes spanning across teams, to identify threats, mitigate vulnerabilities, and ensure the organization remains resilient.
|
By Kovrr
Embracing cyber risk management during a time in which the average cost of a data breach nearly surpasses $5 million is not merely a strategic option; it’s an absolute imperative. This calculated move, however, is not as straightforward as deploying an end-point detection solution, for example, or conducting monthly cybersecurity awareness sessions.
|
By Kovrr
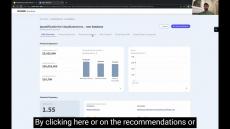
Cyber risk quantification (CRQ) is the process of attributing numerical values to a cyber event's impact on an organization. When defined in financial terms, these values enable enterprises to assess and manage their cyber risks at the operational level.
|
By Kovrr
While each organization faces its own unique set of cyber risks that must be carefully assessed and managed in order to reach a state of resilience, certain events are nearly inevitable in today's threat environment, having the potential to create damaging ripple effects across the global market. Early in 2024, Kovrr's cyber risk quantification models identified these potential cyber incidents and loss scenarios most likely to impact organizations worldwide in the upcoming year.
|
By Kovrr
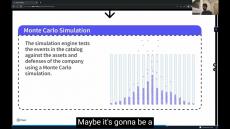
As a part of its ongoing commitment to providing chief information security officers (CISOs) with practicable insights that guide high-level cyber risk management decision-making, Kovrr's latest model update increases the number of yearly trials in its Monte Carlo simulation by 150%.
|
By Kovrr
The evolution of the cyber risk management landscape is constant, and with each passing year, market players find themselves in the position of having to readjust their strategies, whether in brand positioning, cybersecurity, or beyond, to account for these consequent changes. While some of the shifts are welcome, others are less so. Nevertheless, all require careful foresight.
|
By Kovrr
As the cost and frequency of cyber events grow, technologies evolve, and regulatory bodies enact stricter cybersecurity laws on the market, it’s become exceedingly clear that elevating cyber matters to the boardroom is a strategic imperative.
|
By Kovrr
A cybersecurity risk assessment, or cyber risk assessment, is a standardized process that organizations have established along with their implementation of cloud-based technologies to discover the accompanying vulnerabilities and threats. These assessments leverage the available, relevant data to identify the likelihood of various cybersecurity events occurring along with the potential impact should they come to fruition.
|
By Kovrr
Join us for a monthly insightful session where each month we will: Walkthrough our CRQ platform Unveil exciting new product features (when applicable)
|
By Kovrr
Join us for a monthly insightful session where each month we will: Walkthrough our CRQ platform Unveil exciting new product features (when applicable)
|
By Kovrr
Join us for a monthly insightful session where each month we will: Walkthrough our CRQ platform Unveil exciting new product features (when applicable) Conduct Interactive Q&A Session.
|
By Kovrr
Join Kovrr and Dmitriy Sokolovskiy, former CISO at Avid, as he shares his experience and provides highlights and Insights on his CRQ Journey. Some of the topics that Dmitriy will discuss.
|
By Kovrr
On Demand webinar on the topic of Leveraging CRQ for Effective Board Level Decision Making.
|
By Kovrr
The 2022 Verizon Data Breach Investigations Report (DBIR), the fifteenth such report in as many years, leads off with a startling statistic: Credentials are the number one overall attack vector hackers use in data breaches. Use of stolen credentials accounts for nearly half the breaches studied by Verizon, far ahead of phishing and exploit vulnerabilities, which account for 19% and 8% of attacks, respectively. Botnets, the fourth most common entry path for hackers, represent a mere 1% of attacks.
|
By Kovrr
By its nature, cyber risk is dynamic. New events happen and evolve all the time, making it difficult for enterprises to financially quantify their financial exposure to cyber attacks. Around two years ago, for example, distributed denial-of-service (DDoS) attacks were making headlines, and now ransomware has come into heightened focus. It's reasonable to believe that other types of attacks will emerge in another two years and continue to change thereafter.
|
By Kovrr
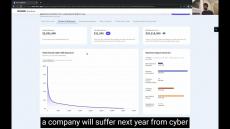
The number of data breaches reported in the first 6 months of 2022 has put this year on track to be the lowest year of reports in the last 5 years for large US corporations. By looking at the rate at which data breach events have been reported so far this year, we predict that the number of events reported is expected to be 15-20% of the number of breaches reported in 2021
- February 2025 (2)
- January 2025 (4)
- December 2024 (1)
- November 2024 (1)
- October 2024 (4)
- September 2024 (3)
- August 2024 (1)
- July 2024 (4)
- June 2024 (3)
- May 2024 (5)
- April 2024 (4)
- March 2024 (3)
- February 2024 (4)
- January 2024 (10)
- December 2023 (5)
- November 2023 (1)
- October 2023 (4)
- September 2023 (1)
- August 2023 (4)
- July 2023 (3)
- June 2023 (2)
- May 2023 (1)
- April 2023 (2)
- March 2023 (4)
- February 2023 (13)
- January 2023 (6)
- December 2022 (2)
- November 2022 (2)
- July 2022 (3)
- June 2022 (1)
- October 2020 (1)
Kovrr financially quantifies cyber risk on demand. Our technology enables decision makers to seamlessly drive actionable cyber risk management decisions.
Kovrr's Quantum Cyber Risk Quantification platform enables decision makers to understand and financially quantify the changing profile of their cyber risk exposure.
Cyber Risk Management Made Easy:
- Communicate Cyber Risk in Financial Terms: Enhance the board and C-Suite’s decision-making process by financially quantifying cyber risk.
- Cybersecurity Investment Optimization: Prioritize and justify cybersecurity investments based on business impacts and risk reduction.
- Measure Cyber Security Programs’ Effectiveness: Assess the ROI of your cybersecurity program and stress test it based on potential risk mitigation actions, thereby supporting better resource allocation.
- 3rd Party Vendors Cyber Risk Exposure Analysis: Financially quantify cyber risk within your supply chain. Gain insights Into 3rd and 4th party exposure.
- Regulatory Compliance and Governance Reporting: Meet increased demands from regulators to continuously quantify and manage cyber risk exposure.
- Cyber Insurance Coverage and Price Optimization: Identify gaps between risk mitigation impact versus risk cyber insurance spending and needed coverage for 1st party and 3rd party.
- Quantitatively Benchmark and Compare your Cyber Risk Exposure: Benchmark to your industry peers and internally compare between different business entities in a consistent, measurable and accurate way.
A cyber risk management platform to quantify custom cyber risk scenarios.