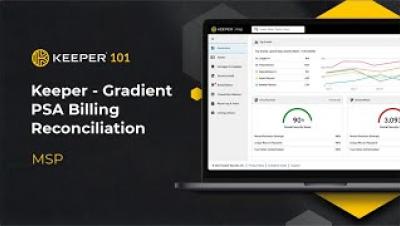
Keeper 101: Keeper - Gradient PSA Billing Reconciliation
Introducing the Keeper-Gradient MSP integration, the powerful solution for Keeper MSP Admins to gain a high-level view of their entire billing process. With this integration, MSPs can streamline their operations and drive business growth. Let's take a closer look at the features and how to set it up. The Gradient MSP integration currently integrates with the most popular PSAs, including Connectwise Manage, Datto Autotask, BMS by Kaseya, and more.