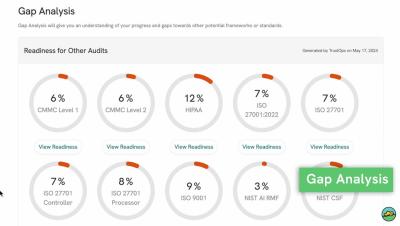
Take advantage of the security and governance features available to you by adding a content source now. From the menu, select Secure & Govern, then Settings, and click Add Cloud Source. Choose the cloud content source you’d like to add and follow the instructions. For additional resources, check out our detailed guides on the Helpdesk. Once a content source is added, Egnyte will begin scanning the repository and alerting you on high severity issues, so you can detect and stop ransomware attacks and receive alerts on anomalous user behavior to prevent data theft.