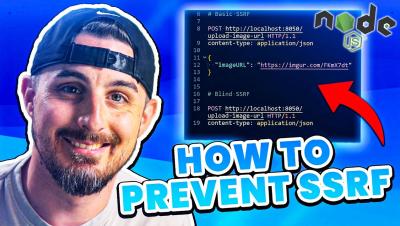
Account Takeover, SQL Injection and DDoS Attack Simulation on APIs
Overview: According to TechTarget, 94% of organizations experience security problems in production APIs, and one in five suffers a data breach. The primary reason is that most tech leaders assume that having a strong authentication and authorisation framework is enough to secure APIs. As a result, cyberattacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise. Join Karthik Krishnamoorthy, CTO and Vivekanand Gopalan Gopalan, VP of Products at Indusface, in this webinar as they demonstrate how APIs can be hacked.