|
By Vivek Chanchal
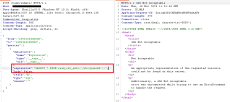
A critical vulnerability, CVE-2024-9264, has been discovered in Grafana, the open-source analytics and visualization platform widely used by organizations worldwide. According to Netlas.io, over 100,000 Grafana instances may be vulnerable globally, with nearly 19,000 in the U.S. alone. This vulnerability poses significant risks, enabling remote code execution (RCE), allowing attackers to execute arbitrary system commands and access sensitive files.
The OWASP Top 10 is a research-based document that raises awareness among developers, organizations, and security professionals on the most critical security risks facing web applications. The latest is the OWASP Top 10 vulnerabilities 2021, released in September 2021 after a 4-year gap. In this article, the OWASP Top 10 vulnerabilities 2021 are explained in detail, along with ways to mitigate each.
|
By Chandan Pani
From GDPR in Europe to CCPA in California, compliance officers and CISOs face a deluge of regulations, standards, and requirements. With every country, industry, and regulator demanding different levels of control, how can teams manage these complex requirements efficiently? In a recent virtual panel discussion, I had the opportunity to join Ashish Tandon, Founder & CEO of Indusface, where I highlighted essential strategies for CISOs to navigate these compliance complexities efficiently.
Security testing aims to find vulnerabilities and security weaknesses in the software/ application. By subjecting the software or application to controlled security scenarios, cyber security testing ensures that the system is adequately prepared to withstand attacks and unforeseen failures. Security experts and testers use different types of security testing to identify potential threats, measure the probability of exploitation of vulnerabilities, and gauge the overall risks facing the software/ app.
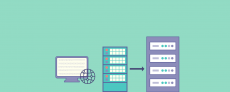
A reverse proxy is a server that sits between the client and the origin server. It accepts requests from clients and forwards them to the appropriate server. It also receives responses from the server and sends them back to the client. A reverse proxy is an essential component of web application infrastructure, providing a layer of abstraction between clients and origin servers to help optimize traffic routing and improve performance and security.
|
By Chandan Pani
Compliance is a critical concern for businesses today, but navigating the rules can be overwhelming. With regulations constantly evolving, many organizations struggle to keep up. I had the opportunity to participate in a recent virtual panel with Ashish Tandon, Founder & CEO of Indusface. Over the years, I have consulted with multiple large enterprises across geographies and industries. Below are the top challenges that they face as far as compliance is concerned.
|
By Vivek Chanchal
A new series of vulnerabilities in the Common Unix Printing System (CUPS) threatens numerous Linux systems, potentially allowing remote code execution (RCE). This affects a wide range of platforms, including Debian, Red Hat, SUSE and macOS. The vulnerabilities—tracked as CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177—are believed to endanger over 76,000 devices, with estimates suggesting up to 300,000 could be affected.
A zero-day flaw in MOVEit software exposed the data of 66.4 million individuals, revealing businesses are increasingly vulnerable to cyberattacks. Applications, which manage sensitive data, are prime targets for these threats. Compliance regulations recognize the risks and establish guidelines aimed at ensuring applications meet data protection, privacy, and overall security. PCI DSS v4.0 for example introduces 64 new requirements including strict security measures to protect public-facing applications.
|
By Pavithra Hanchagaiah
A high severity OS command injection vulnerability, CVE-2024-8190, has been found in Ivanti Cloud Services Appliance (CSA) versions 4.6 Patch 518 and earlier. This flaw allows attackers with admin access to remotely execute malicious commands, potentially taking full control of the system. Ivanti has already released updates, but this command injection vulnerability is actively exploited in the wild, making immediate action critical.
The State of Application Security report shows that over 2.37 billion attacks were blocked on AppTrana WAAP from April 1, 2024, to June 30, 2024. Attacks targeting vulnerabilities surged by 1,200% in Q2 2024 compared to last year, an alarming fact. This sharp rise highlights that vulnerabilities are the prime target. Moreover, they are now easily exploitable thanks to readily available scripts on known vulnerabilities. This could be because of rapid adoption of AI and LLM models even among hackers.
|
By Indusface
Explore how a Web Application Firewall (WAF) protects websites by blocking malicious attacks using key methods, including filtering traffic and preventing threats like SQL injections and XSS.
|
By Indusface
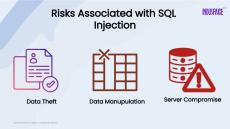
SQL injection is a type of attack where malicious SQL code is inserted into a query, allowing attackers to access or manipulate a website's database. Learn the best practices to prevent SQL injection and safeguard your web applications.
|
By Indusface
Over 1 billion known malware threats exist, with an alarming 17 million new variants emerging each month! Malware targeting customer-facing websites and API applications poses significant risks, including compliance violations, defacements, and even blacklisting. In this webinar, join Vivekanand Gopalan, VP of Products at Indusface, as he shares effective strategies for safeguarding websites and APIs against malware.
|
By Indusface
It’s considered a best practice to regularly conduct VAPT to identify and fix vulnerabilities in systems, applications, and networks, ensuring robust security.
|
By Indusface
WAAP encompasses a comprehensive suite of tools, technologies, and practices that detect, prevent, and mitigate attacks, such as cross-site scripting (XSS), SQL injection, and API abuse. By implementing a robust WAAP, organizations can fortify their applications and APIs, safeguard sensitive data, and uphold the trust of their users in an ever-evolving threat landscape. Examine the functionality and effectiveness of the leading WAAP & WAF software, along with their key features, reviews, ratings, and insights into who they are best suited for.
|
By Indusface
Overview: Picture this: Your website included a 3rdparty component (such as a WordPress plug-in), and hackers used that as a backdoor to infiltrate your systems, which were secure on their own. This is a supply chain attack. Pollyfillio attack is a recent example of this where 100,000 websites were impacted last month. In this webinar, Vivekanand Gopalan (VP of Products - Indusface) and Phani Deepak Akella (VP of Marketing - Indusface) discuss strategy and tactics to protect your applications from supply chain attacks.
|
By Indusface
Discover how DDoS mitigation works to protect your website from attacks. Learn about the strategies used to detect and neutralize threats, ensuring uninterrupted service.
|
By Indusface
Execution of malicious scripts was responsible for 52% of 75,000 cyber incidents. These scripts are typically used to harvest data from customer-facing websites and APIs. 60%+ such attacks target SMEs. An alarming situation when you consider the limited resource and tool budgets allocated for website and API security. A managed, enterprise-class application security offering with 24x7 SOC is, therefore, the need of the hour for SMBs.
|
By Indusface
Million+ unique IPs hit your web or API server with one or two requests per minute. Default rate-limits fail immediately, and your server is down. 50% of the DDoS attacks employ botnets for launching such attacks. In this live attack simulation, join Karthik Krishnamoorthy (CTO of Indusface) and Vivek Gopalan (VP of Products of Indusface), as they demonstrate advanced AI-powered DDoS mitigation while minimizing false positive blocks.
|
By Indusface
With the rapid explosion of APIs and the huge exchange of information through APIs, every organization should be concerned about how secure are these APIs? Download this whitepaper to understand the evolving cyber threats to APIs and how to mitigate them.
|
By Indusface
A lot of vulnerabilities notoriously registered themselves in the Internet hall of fame, continuing to haunt giant organizations. When so much is happening around, we are sure you would have missed out on some of the key stories. Read this eBook to stay updated on everything important.
|
By Indusface
Bots are everywhere in today's technology. The fundamental challenge is to detect and block the malicious bots that could destroy your business. Download our whitepaper to understand the importance of a good bot management solution.
|
By Indusface
Web-based attacks are the most common attack faced by many businesses regardless of size. Want to identify the vulnerabilities most prevalent to your business and mitigate them?
|
By Indusface
Whatever may be the reason behind the DDoS attacks, this attack is here to stay and almost anyone can become a victim of DDoS attacks. The key piece to address this attack is the DDoS mitigation plan that organizations have in place.
|
By Indusface
In this time of increasing complex cyber-attacks, you should look across the multiple security vulnerabilities to investigate and mitigate risks to keep your organization safe. This eBook reviews the real security attacks that have exploited vulnerabilities and provides a synopsis of facts and fixes.
|
By Indusface
Managed WAF is the best solution available to protect applications from attacks. In this whitepaper, we will try to explore why this is the case and how can WAF be effectively deployed to ensure better efficacy?
|
By Indusface
Website vulnerabilities have become a security nightmare for most businesses. Whether you're an entrepreneur, a CIO, a director of security, a CTO, or something in between, understanding and evaluating risks is critical. And that's exactly where this eBook, can help you.
- November 2024 (7)
- October 2024 (5)
- September 2024 (5)
- August 2024 (10)
- July 2024 (12)
- June 2024 (6)
- May 2024 (8)
- April 2024 (9)
- March 2024 (9)
- February 2024 (10)
- January 2024 (8)
- December 2023 (6)
- November 2023 (7)
- October 2023 (9)
- September 2023 (10)
- August 2023 (9)
- July 2023 (12)
- June 2023 (7)
- May 2023 (11)
- April 2023 (9)
- March 2023 (15)
- February 2023 (13)
- January 2023 (6)
- December 2022 (1)
- November 2022 (4)
- October 2022 (10)
- September 2022 (10)
- August 2022 (5)
- July 2022 (1)
- April 2022 (6)
- March 2022 (1)
- February 2022 (6)
- January 2022 (3)
Secure web applications & APIs with ease. Get fully managed web app firewall & scanner to prevent DDoS & Bot attacks.
Indusface is a SaaS company that secures critical Web applications of 3000+ global customers using its award-winning platform that integrates a Web application scanner, Web application firewall, CDN, and threat information engine. Indusface is funded by Tata Capital Growth Fund.
We make it easy for you to secure your Web and Mobile Applications:
- Managed Web Application and API Protection: Risk Based Fully Managed Web Application and API protection with real time protection against OWASP exploits, DDOS attacks, Bot Mitigation and Zero Day attacks with 24x7 support from security experts.
- Comprehensive application vulnerability detection: Automated DAST Scanner combined with on demand Manual Penetration Testing , False positive removal via manual verification with 24x7 support from Security experts.
- Comprehensive Mobile Application vulnerability detection: In depth Pen-testing with multiplatform coverage including iOS, Android, Windows
- Powerful digital certificates for secure communication: Standard, EV, UCC multidomain & Wildcard certificates for your applications.