FINRA Warns of Rising Risks as Third-Party Cyberattacks Threaten Financial Services
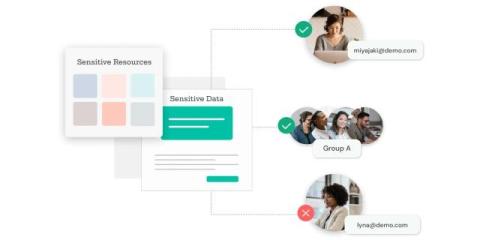
Earlier this month, the Financial Industry Regulatory Authority (FINRA) posted a cybersecurity advisory highlighting the recent cybersecurity risks of third parties impacting its members and financial services organizations. The recently released Trustwave SpiderLabs 2024 Trustwave Risk Radar Report: Financial Services Sector underscores FINRA's concern about the escalating threat landscape facing the financial industry.