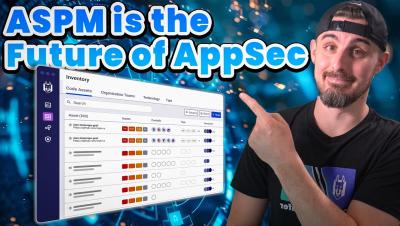
Dependency Confusion Vulnerability Exposure Protections In GitGuardian SCA
Supply chain security can be a struggle. The GitGuardian Source Composition Analysis module scans your project's dependencies, comparing them against public repos. If it finds any matches between your internal packages and public ones, it flags them as potential dependency confusion risks.